Atola TaskForce
Image. Anything. Fast. What makes TaskForce the ultimate forensic imager
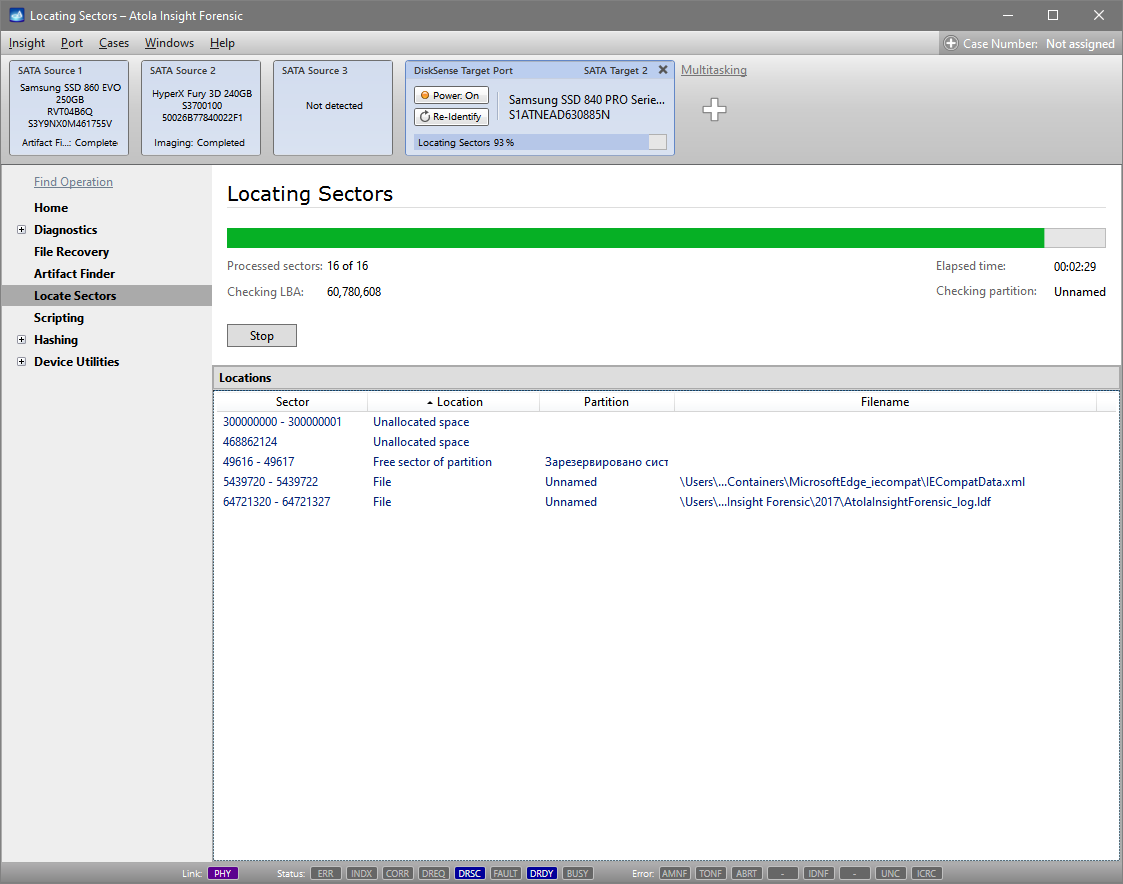
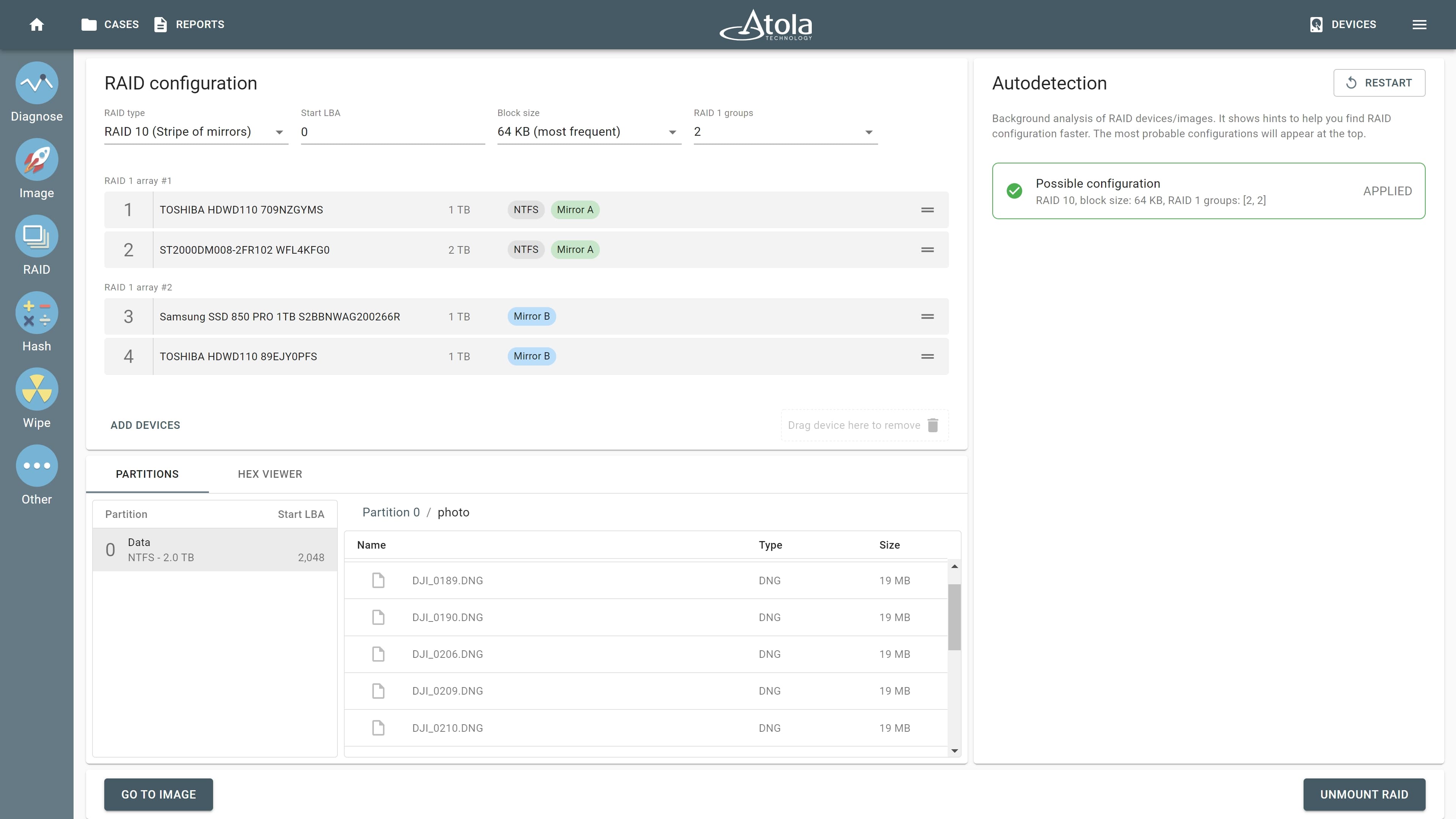
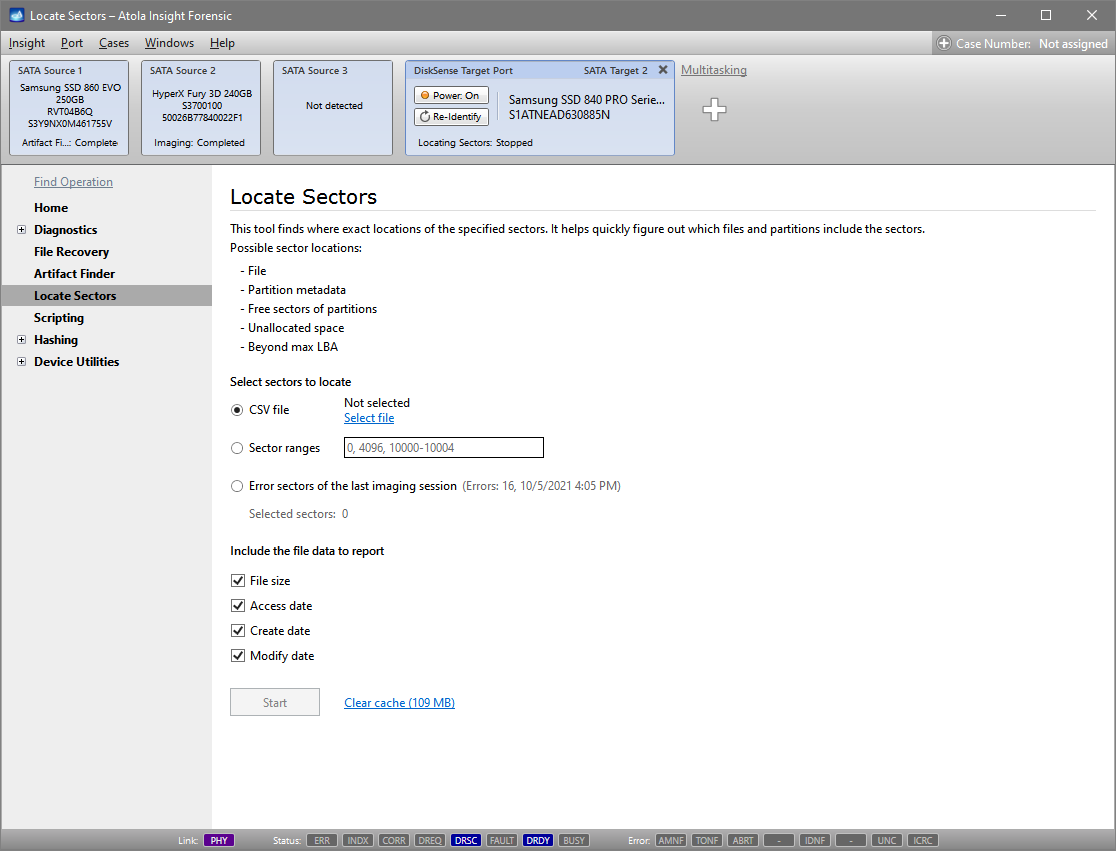
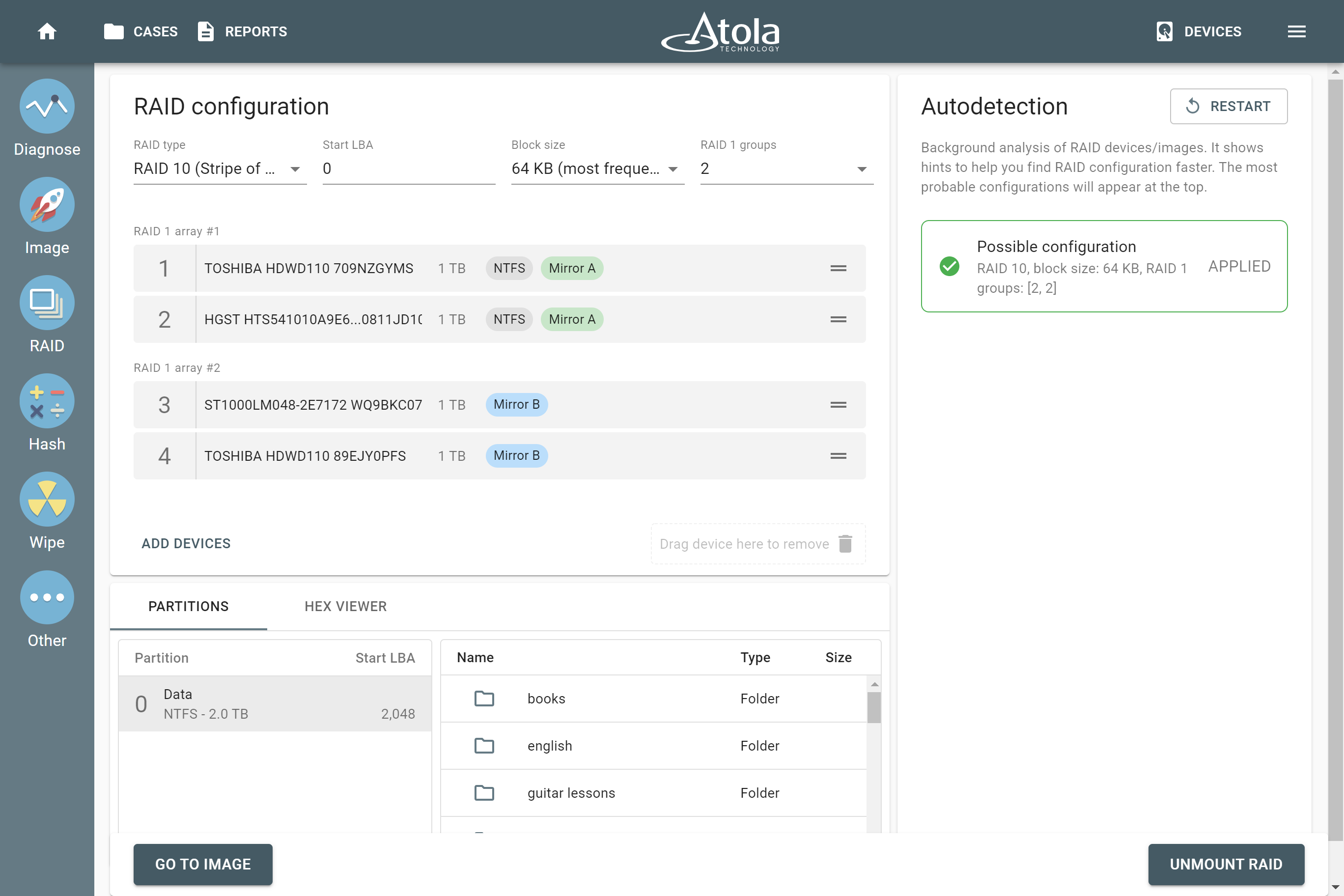
Atola’s high-performance TaskForce forensic imager has a well-developed imaging functionality that performs a huge variety of acquisition-related jobs. Not only does it assemble, identify RAID configuration and image RAID arrays. TaskForce also safely handles damaged evidence drives, verifies data on good and bad media, performs selective imaging, has a special zero-click imaging mode on its 17 source ports, etc. In this blog, we will touch on all of these and other imaging options that make TaskForce an imager that exceeds your expectations. Optimize your performance TaskForce is equipped with a variety of time-saving features that boost your productivity, making your work with evidence drives simple and effective. With its 18 Read more…