Atola TaskForce
Imaging RAID 5 array with errors on multiple drives
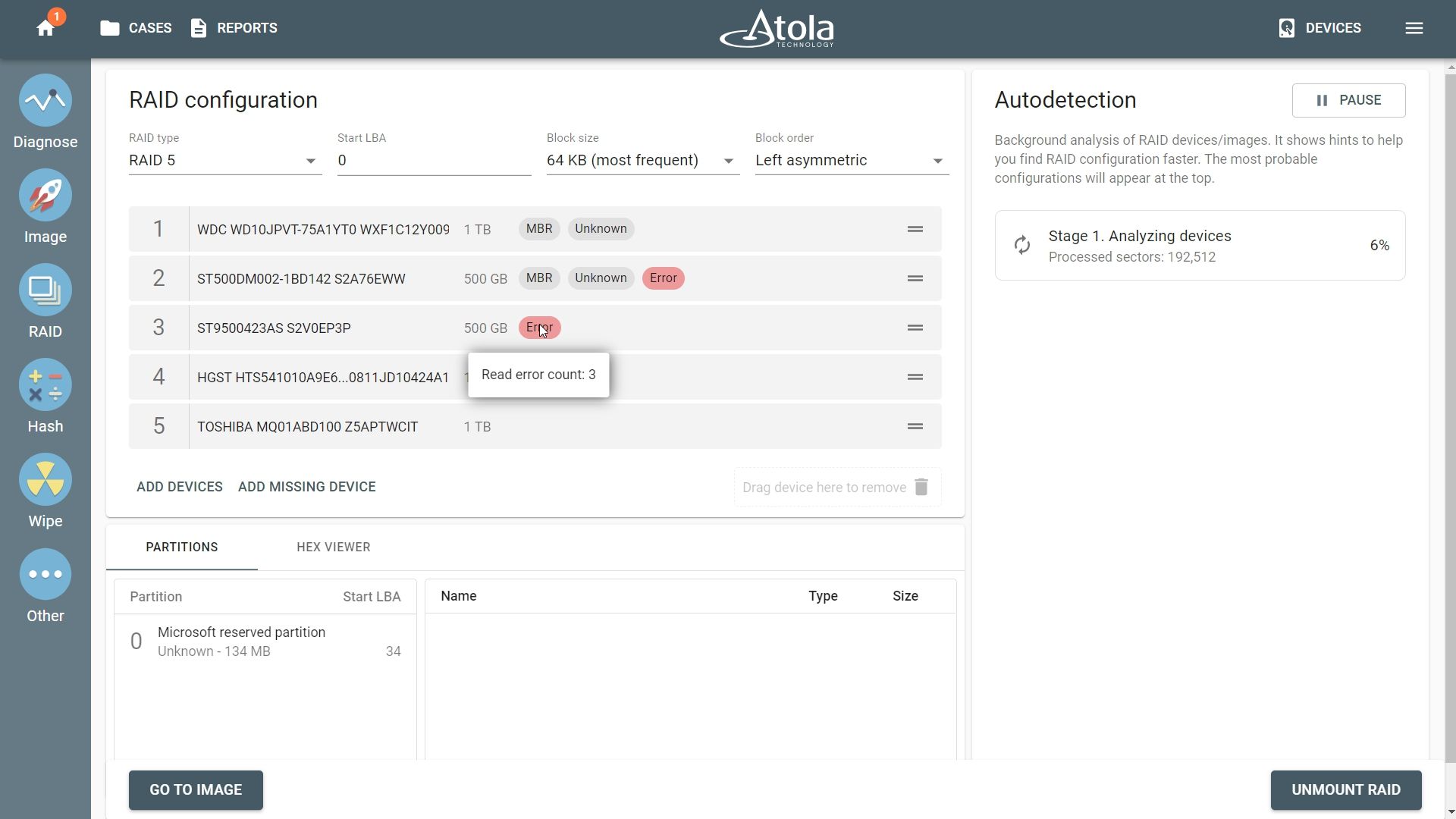
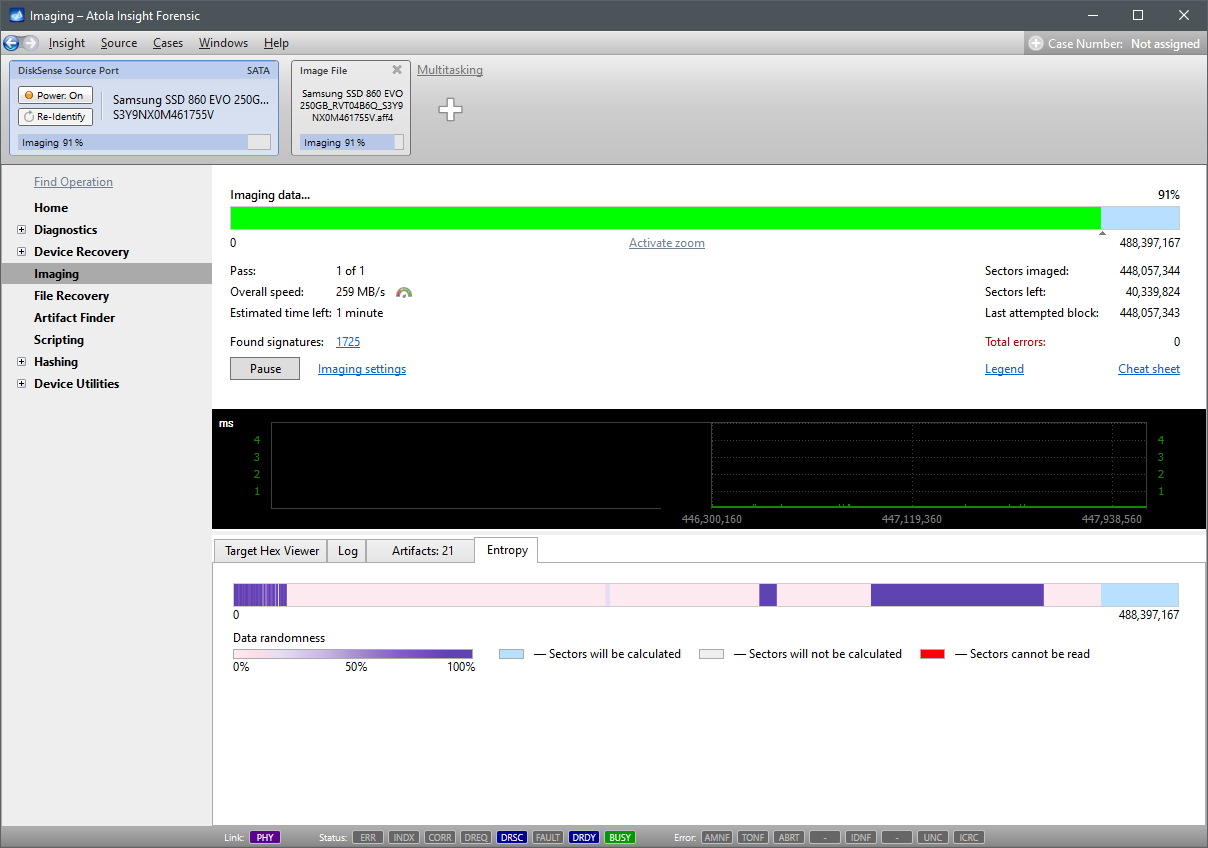
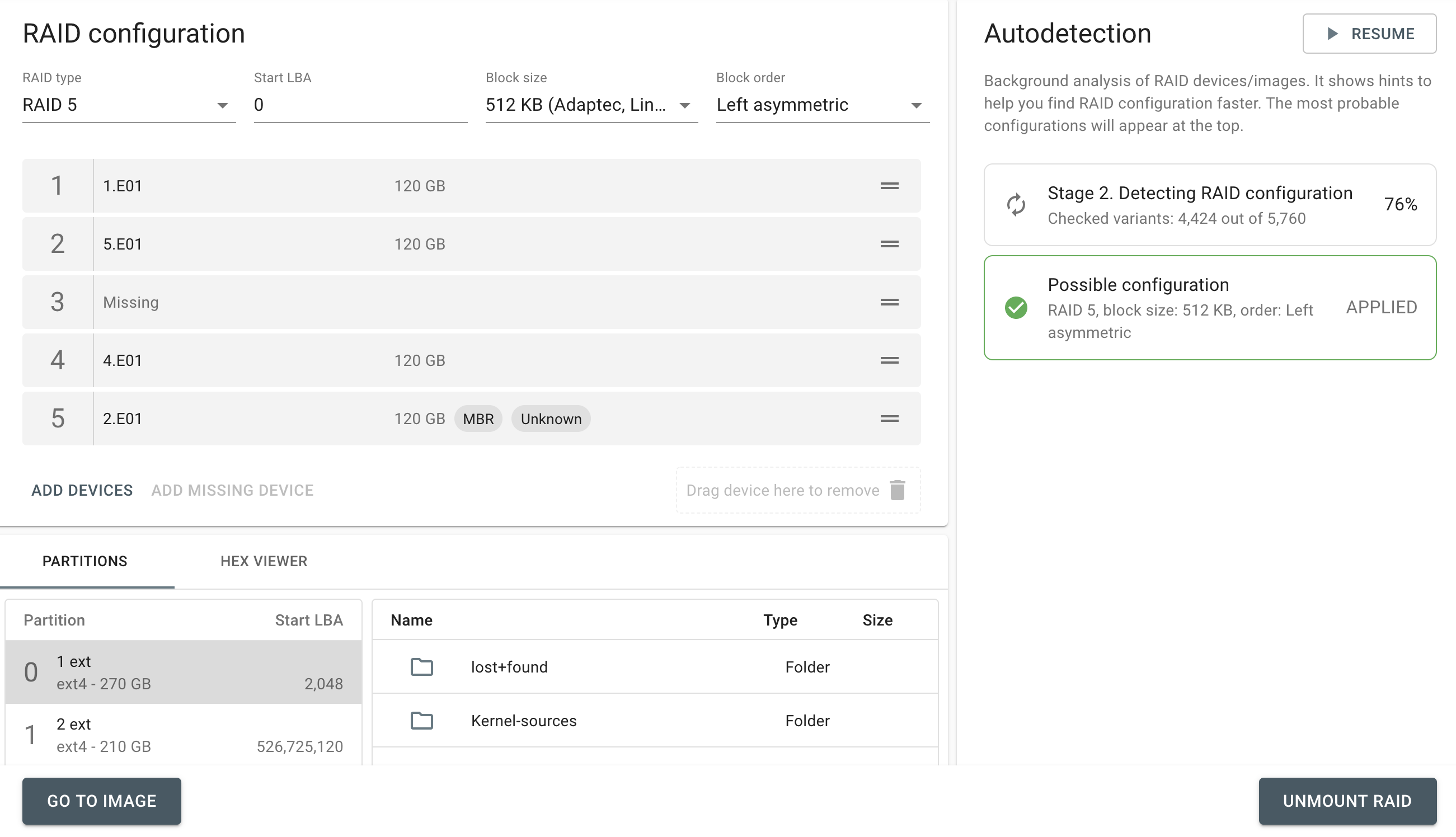
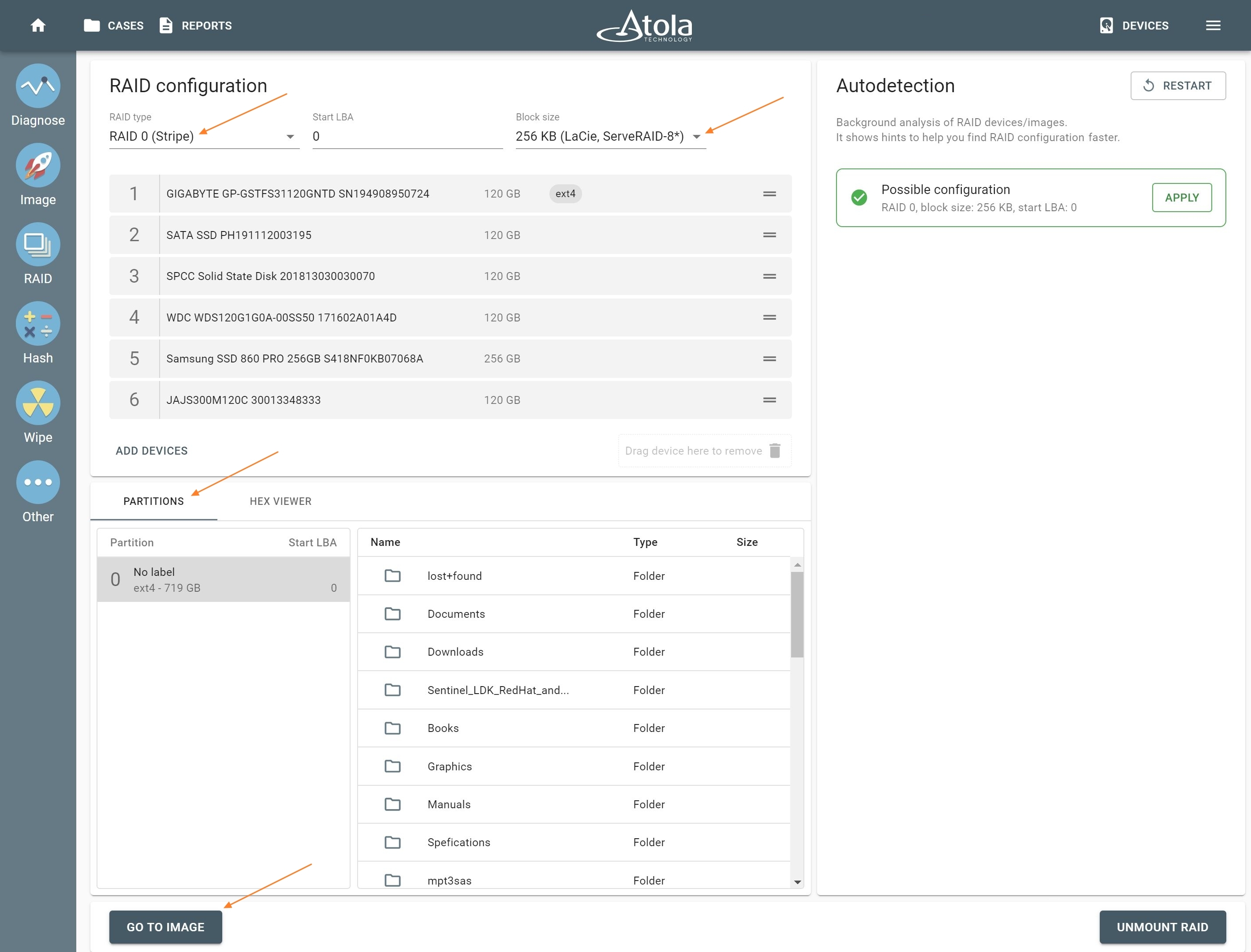
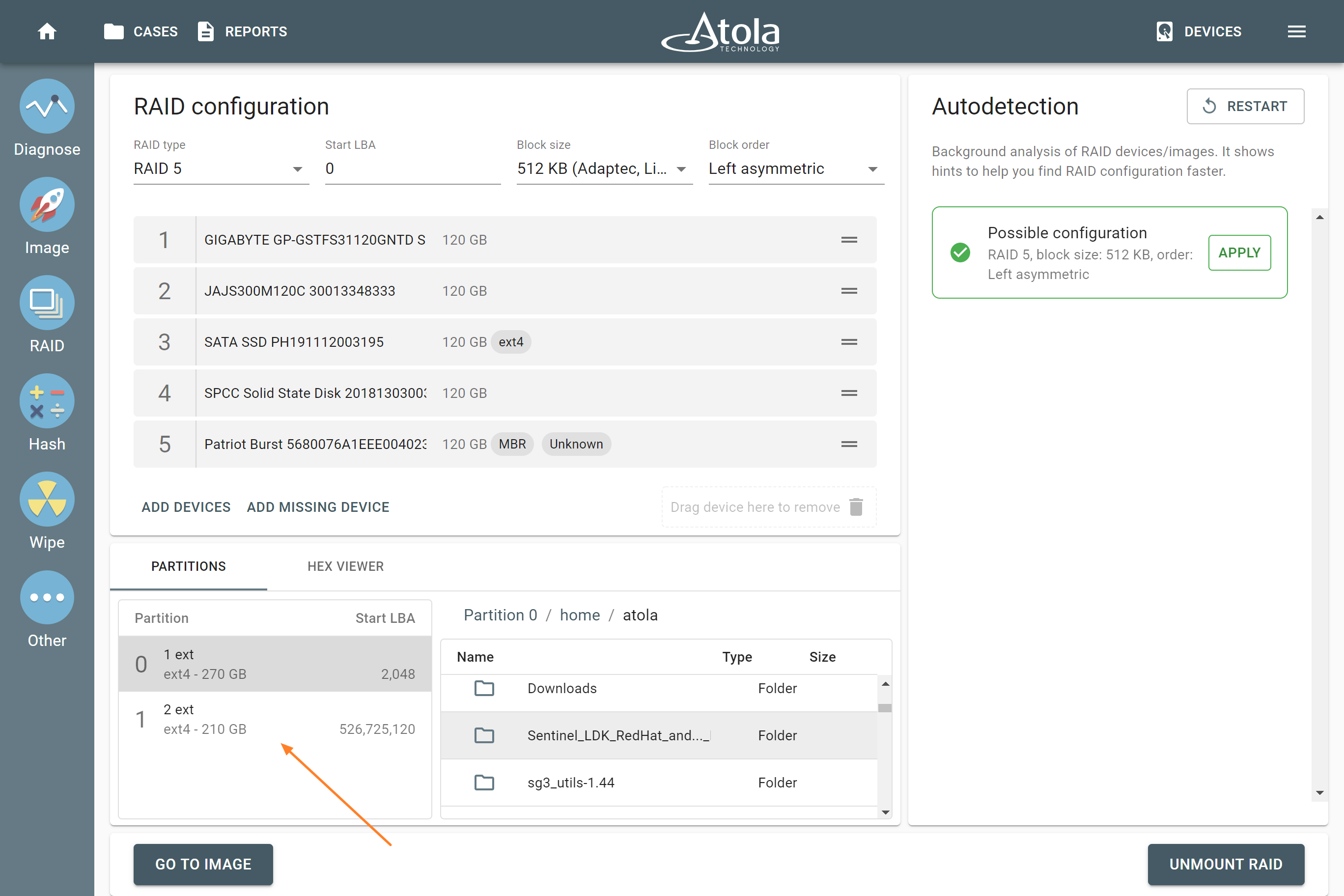
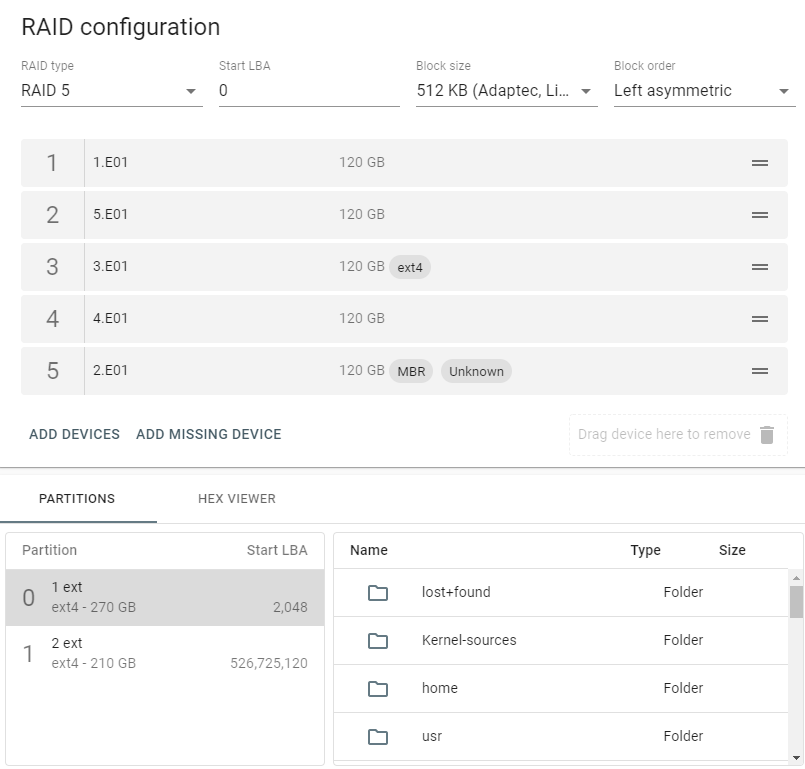
When imaging RAID 5 array with errors on multiple drives, Atola TaskForce is still able to detect its parameters and image the whole RAID. Let’s examine a case with a RAID 5 consisting of 5 drives, two of which have bad sectors. Reassembling RAID 5 array with errors on multiple drives Click the RAID button in the left-side taskbar and select the drives that make up the RAID array. TaskForce autodetection module starts running immediately upon selection of the RAID members. In Stage 1, TaskForce reads data on the drives to identify the RAID type. In case it runs across an error, it displays an Error tag next to the corresponding RAID Read more…