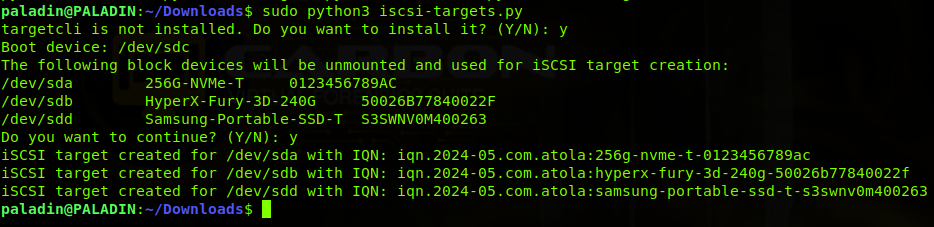
We’re going live with a new update for Atola Insight Forensic. Version 5.3 is packed with new features, has received a decent performance boost, and broadened its multitasking capabilities.
Here’s our top picks:
- Cryptocurrency artifacts search: BIP39 mnemonic phrase, Bitcoin and Ethereum wallet addresses.
- New wiping methods for NVMe drives: Format NVM and Sanitize.
- Multi-launch of Automatic checkup, Artifact finder, Locate sectors, and Calculate hash.
Let us show you the new opportunities they bring and how these new features can simplify your work!
Search cryptocurrency artifacts on the fly
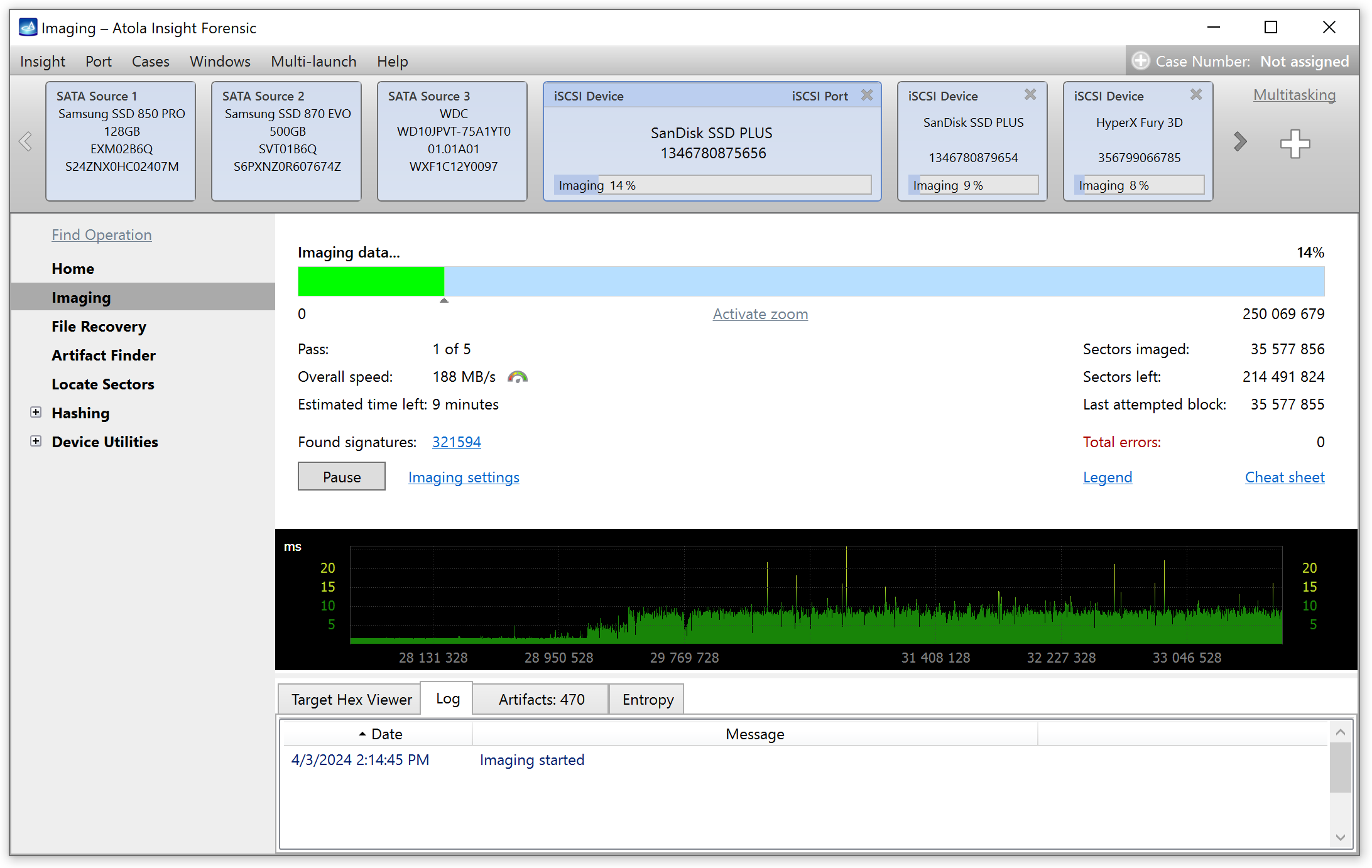
Insight Forensic is much more than simple imaging software. It supports copying of damaged drives and manages 3 parallel imaging sessions with ease. To speed up evidence search and optimize acquisition process, it performs sector-level artifact detection during imaging.
In addition to emails, IP and MAC addresses, GPS and URLs, credit card and phone numbers, keywords and regular expressions, Insight Forensic 5.3 can now perform a live search of cryptocurrency artifacts:
- BIP39 mnemonic phrase,
- Bitcoin wallet address,
- Ethereum wallet address.
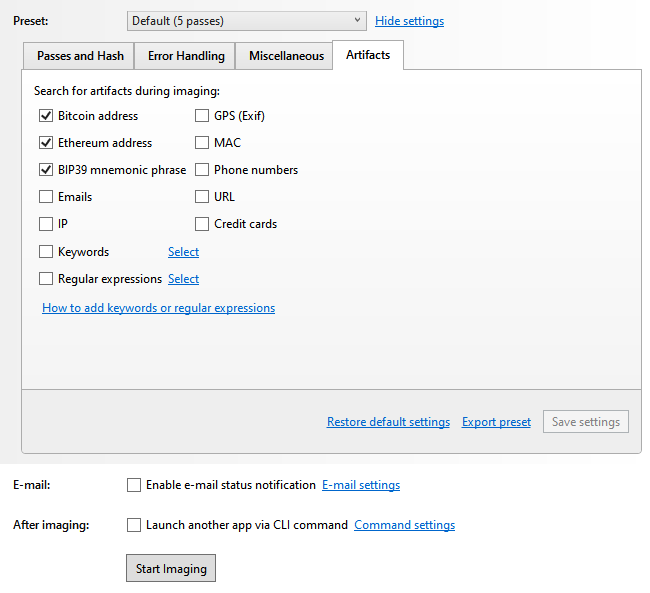
Artifacts type selection in the imaging settings.
Bitcoin wallet address search supports P2PKH, P2SH, P2WPKH, and P2TR types.
Search options for BIP39 mnemonic phrase are:
- Case-insensitive search,
- ASCII, UTF-8, UTF-16 encodings,
- English and Portuguese languages.
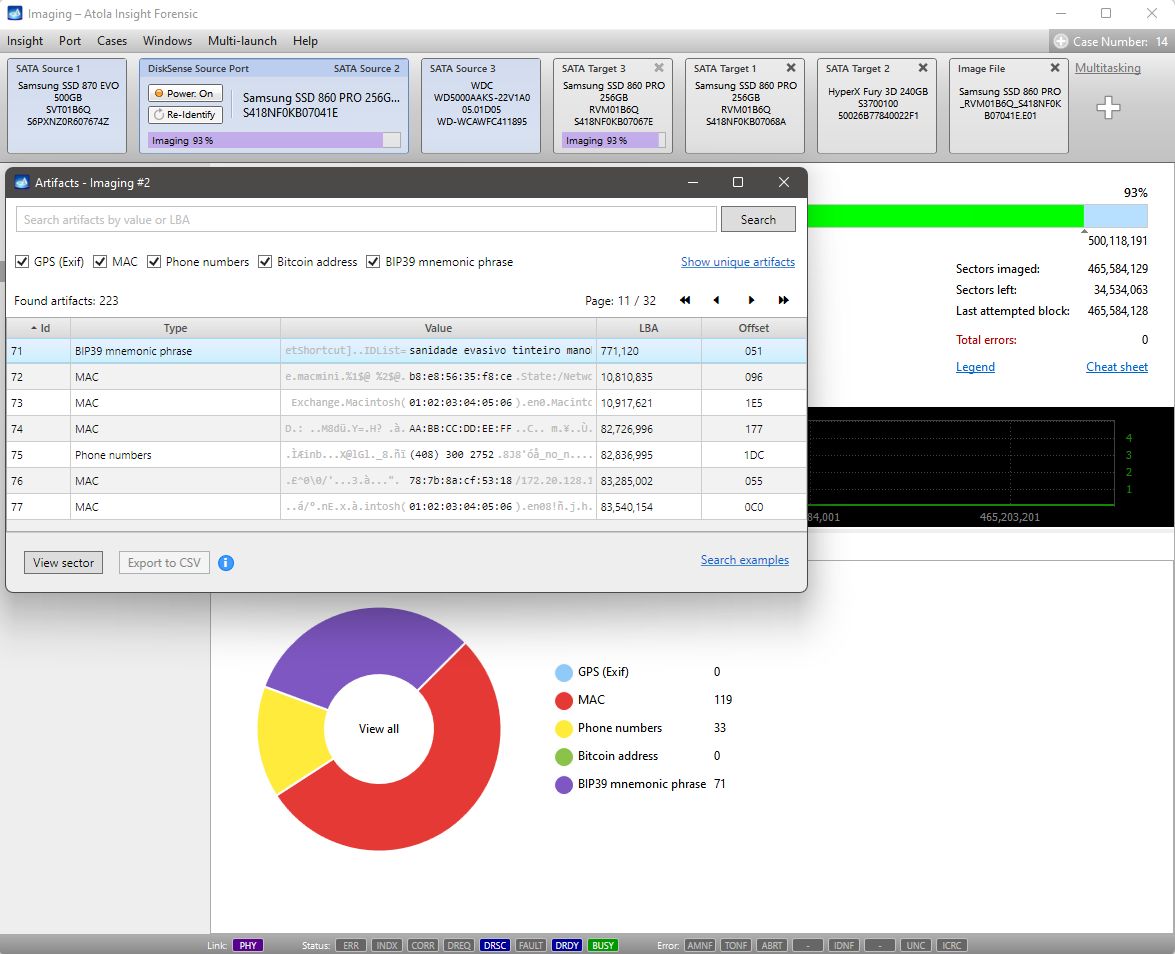
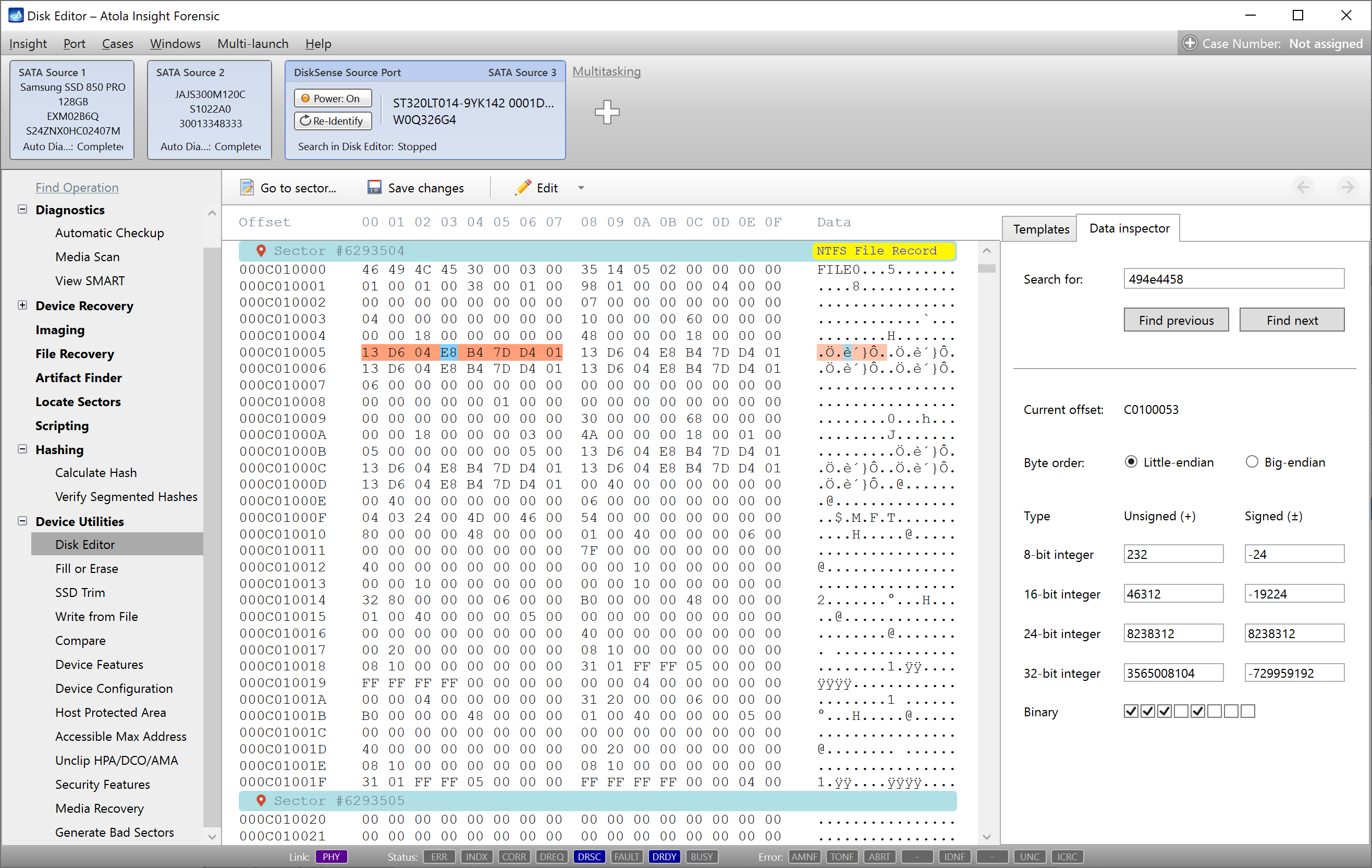
The BIP39 mnemonic phrase found during imaging.
Enhanced Artifact finder provides preliminary overview of evidence on a drive as you image it.
Securely wipe NVMe drives with Sanitize and Format NVM
For secure wiping of NVMe M.2 drives with Fill or Erase command, we’ve added support for two new methods based on NVMe 1.4 specification:
- Format NVM
- Sanitize
Format NVM method uses SSD controller’s internal wiping algorithm according to FORMAT NVM command specified in NVM Express Base Specification.
You can choose between two erase modes, both of which follow NVMe standard:
- If you select Perform Cryptographic Format NVM checkbox, all the user data from NVMe drive will be erased cryptographically. This is accomplished by deleting the encryption key. If the drive doesn’t support cryptographic erase, this option is unavailable.
If you clear Perform Cryptographic Format NVM checkbox, all the user data from NVMe drive will be erased, the contents of the user data after the erase is indeterminate. The user data may be filled with zeroes, ones etc., depending on the manufacturer’s wiping algorithm.
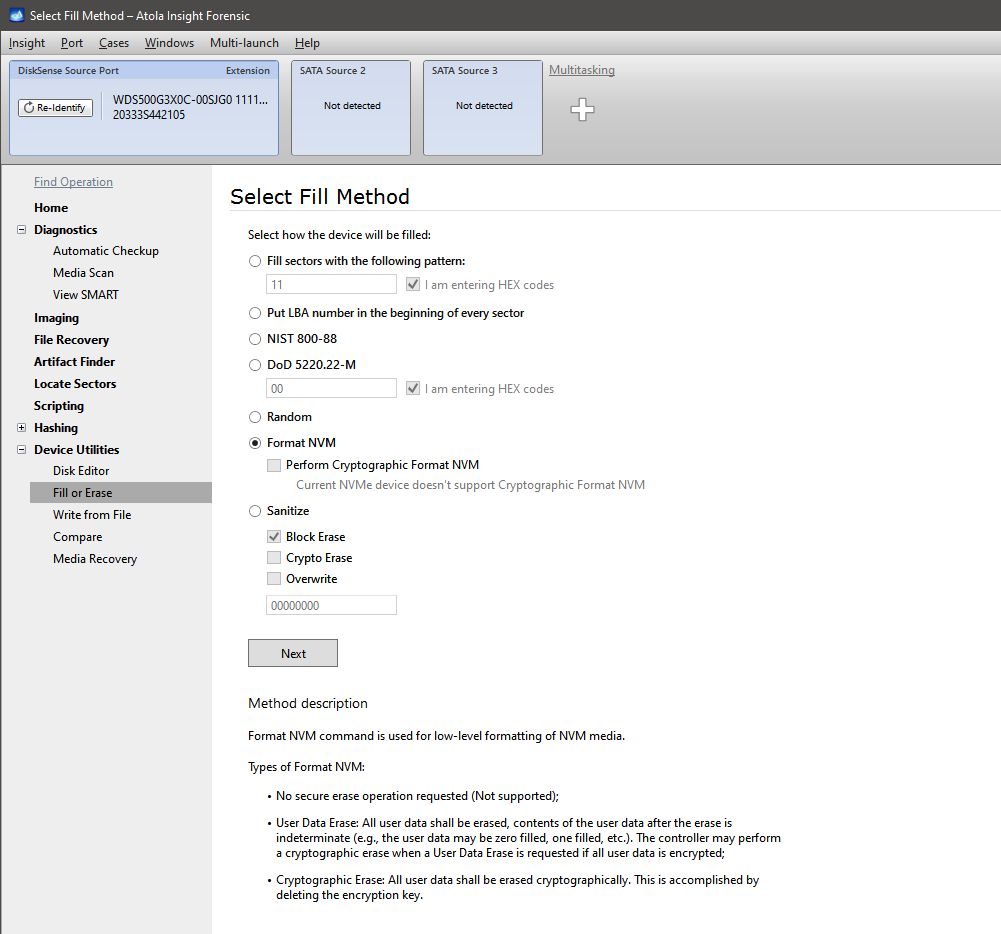
Format NVM command in the Fill or Erase menu.
Sanitize method applies the SSD controller’s internal wiping algorithm to securely erase all user data from NVMe drive, according to SANITIZE command specified in NVM Express Base Specification.
This method lets you select different options for altering user data in all locations on the drive in which user data may be stored:
- Block Erase uses a low-level block erase method specific to the media.
- Crypto Erase changes the media encryption keys.
- Overwrite writes a fixed data pattern.
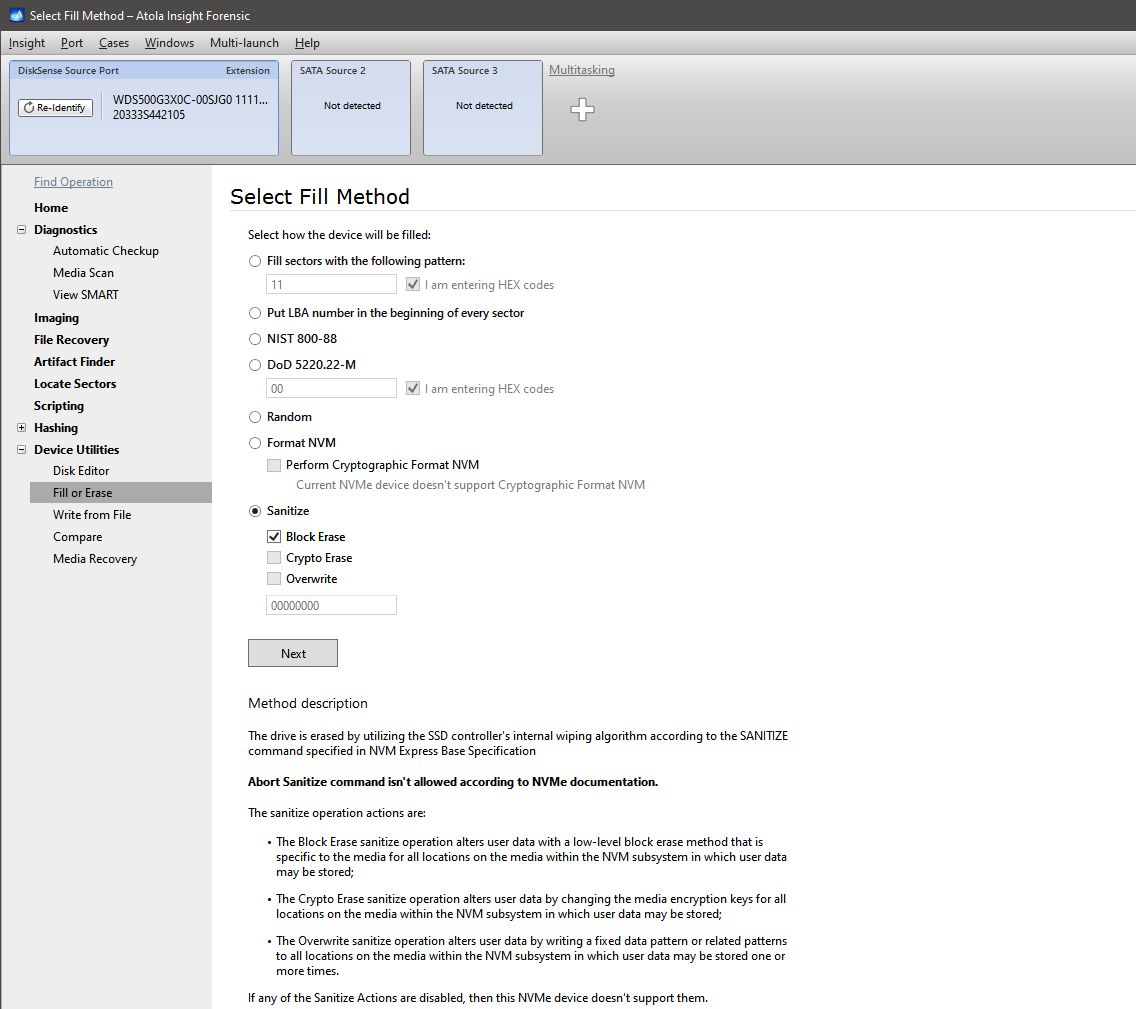
Sanitize command in the Fill or Erase menu.
Launch more tasks with fewer clicks
We introduced Multi-launch for simultaneous wiping of up to 7 devices in Insight Forensic version 5.2.
But now, with Insight 5.3, you have even more commands in the Multi-launch menu.
Run similar tasks on all connected devices at once – in just a few clicks:
- Search artifacts with Artifact Finder.
- Diagnose drives with Automatic Checkup.
- Calculate Hash on up to 7 devices simultaneously.
- With Locate sectors command, find out to which files certain sets of sector ranges belong throughout all connected drives.
Multi-launching Artifact Finder for all connected devices.
To boost multitasking productivity even more, we’ve added the Detect all devices option to the Port menu. With this command, you can power up and identify all attached drives at once.
Detect all devices at the start to save time and effort down the line.
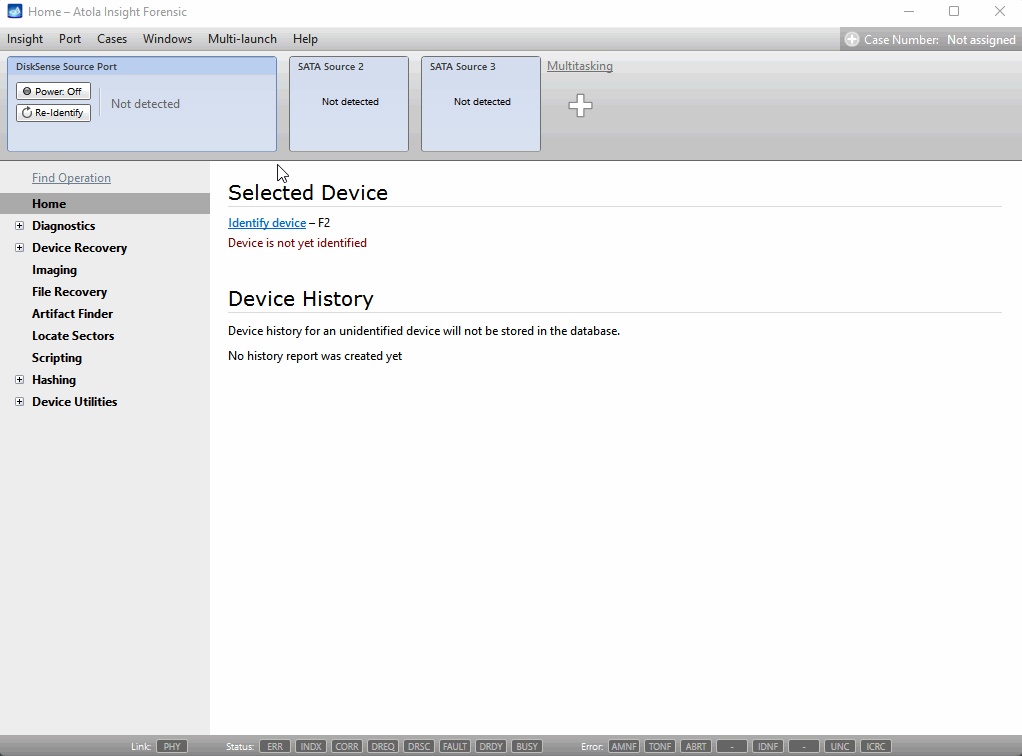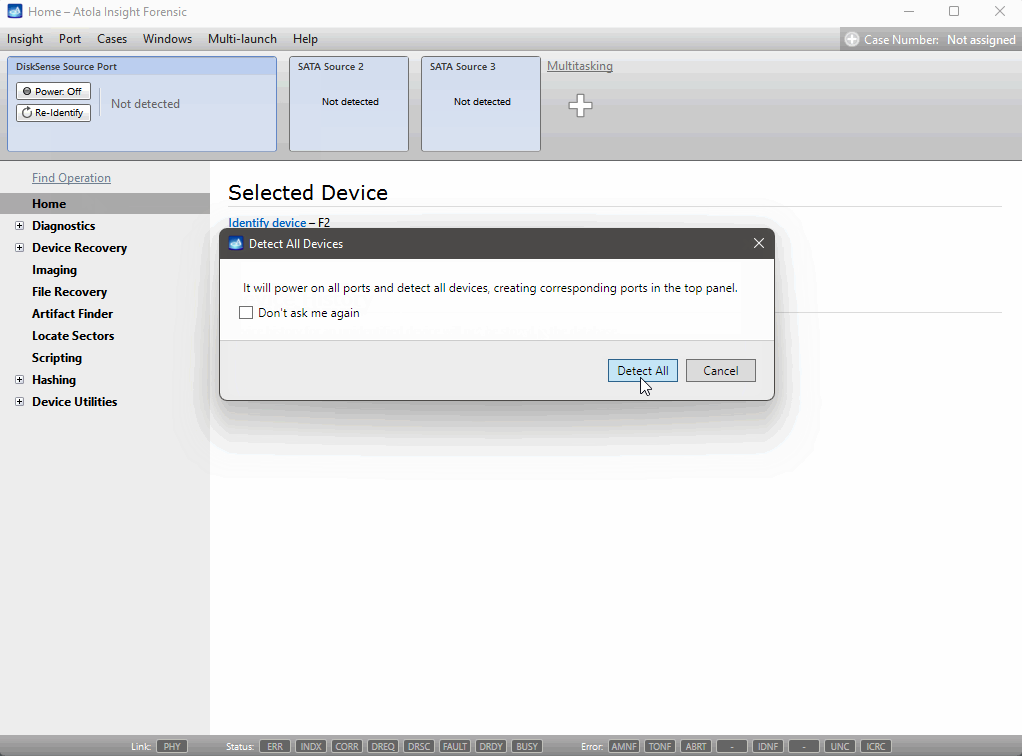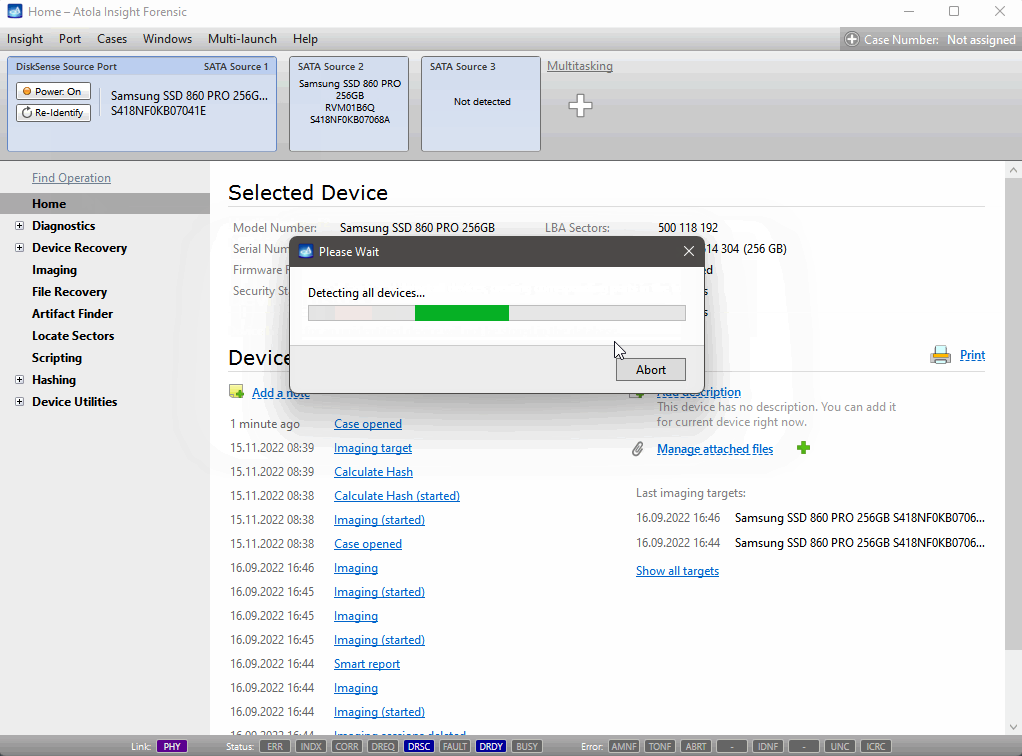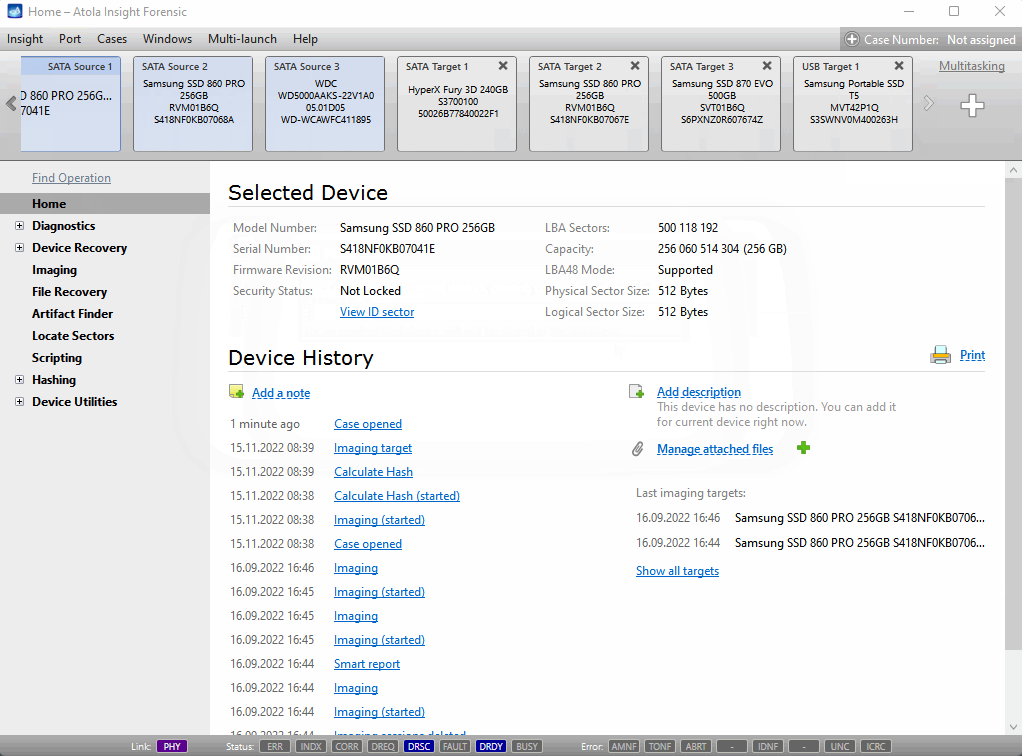
Detect All Devices command in the Port menu.
Calculate hash up to 110% faster
We’ve rebuilt our hashing algorithms, so you could calculate hashes even faster. As a result, hash calculation performance has increased by up to 110% depending on hash type.
See the speed comparison in MB/s of hash calculation on NVMe drives:
| Hash type | Insight 5.2 | Insight 5.3 | Increase |
| MD-5 | 513 | 545 | 6.2% |
| SHA-1 | 482 | 762 | 58.1% |
| SHA-256 | 218 | 359 | 64.7% |
| SHA-512 | 251 | 534 | 112.8% |
| MD5 and SHA-1 | 451 | 525 | 16.4% |
| MD5 and SHA-256 | 213 | 349 | 63.9% |
A decent productivity boost!
Insight Forensic 5.3 Changelog
New Features
Imaging:
- Live search of new cryptocurrency artifacts: BIP39 mnemonic phrase, Bitcoin, and Ethereum wallet address.
- New setting: Limit SATA target drive via AMA.
- Hash calculation performance increase up to 110% depending on hash type.
- Autosave of parameters: What to image, Email notifications, After imaging.
- Launch of CLI app after imaging option can also be enabled during the running imaging session.
- New non-modal window for CLI app launched after imaging
- DiskSense 2 unit only: Imaging to E01 file on target drive.
Multi-launch menu. Support of quick launch for these operations:
- Automatic Checkup (drive diagnostics)
- Artifact Finder
- Locate Sectors
- Calculate Hash
New menu point: Detect all devices. It powers all attached drives up and identifies them.
Fill or Erase. New wiping methods for NVMe drives based on NVMe 1.4 specification:
- Format NVM
- Sanitize
Artifact Finder. New cryptocurrency artifacts types:
- BIP39 mnemonic phrase: case-insensitive search, ASCII, UTF-8, UTF-16 encodings, English and Portuguese languages.
- Bitcoin wallet address: P2PKH, P2SH, P2WPKH, P2TR types.
- Ethereum wallet address.
Automatic checkup:
- Firmware. AMA max address detection.
- Firmware. Better Reading for vendor-specific SMART attributes of various SSD models.
- File system. Improvements for exFAT partitions.
AMA (Accessible Max Address) – a new operation in Device Utilities.
DiskSense 2 unit only. New source type: E01 image file on source drive.
Bugfixes
Specific drive support:
- Password recovery: Unknown password removal was failing for a few Seagate drive models.
- Inability to read Micron NVMe SSD, Model MTFDHBA256TCK-1AS1AABHA.
Imaging:
- USB drives with s/n above 70 characters. Failing to save file signatures & artifacts found during imaging.
- Lack of total speed indication during the growth of a non-sparse target image file.
- Several minor issues when creating an imaging map via Custom Map Manager.
File system analysis:
- Possible Incorrect detection of HFS+ partition size on large external drives.
- Rare FAT32 parsing issue when manually creating custom imaging map.
- Unable to parse FAT32 partition from HeimVision DVRs
Case management:
- Too long case folder name for USB devices with abnormally long serial numbers.
- Case import. USB Vendor ID information was missing.
- Several errors when having lack of free space in Work Folder.
- Markup issues of Locate sectors case report when saving or printing to PDF.
Endless reoccurring ”Hasp error 7” when there are no DiskSense units found on the network.
Inability to open image file with enabled read-only attribute.
EXT operation LED was not blinking during running operation.
Source device selection window. A few cases when source devices were not correctly powering off when one closes the window.
DiskSense 2 unit only:
- Impossible to identify IDE drive in Slave mode.
- Rare connectivity issue via ETH2 network port.
- Small interface issue with manual power up of IDE drive
Download
To get access to all new features, download Atola Insight Forensic 5.3 from our website.
Where to buy
To order Atola DiskSense 2 hardware unit or extend your subscription, contact Atola Technology directly or find a distributor near you.
To get more information about Atola Insight Forensic or to discuss the details, please contact Atola Technology sales department:
- Call us: +1 888 540 2010, +1 416 833 3501 10AM-6PM ET
- Or email us
- TaskForce 2024.9 update – Templates for target files - September 26, 2024
- E01 vs AFF4: Which image format is faster? - July 9, 2024
- Image Synology NAS RAIDs with TaskForce 2024.6 - June 27, 2024