Atola Insight Forensic
Search cryptocurrency artifacts and wipe NVMe drives with Insight Forensic 5.3
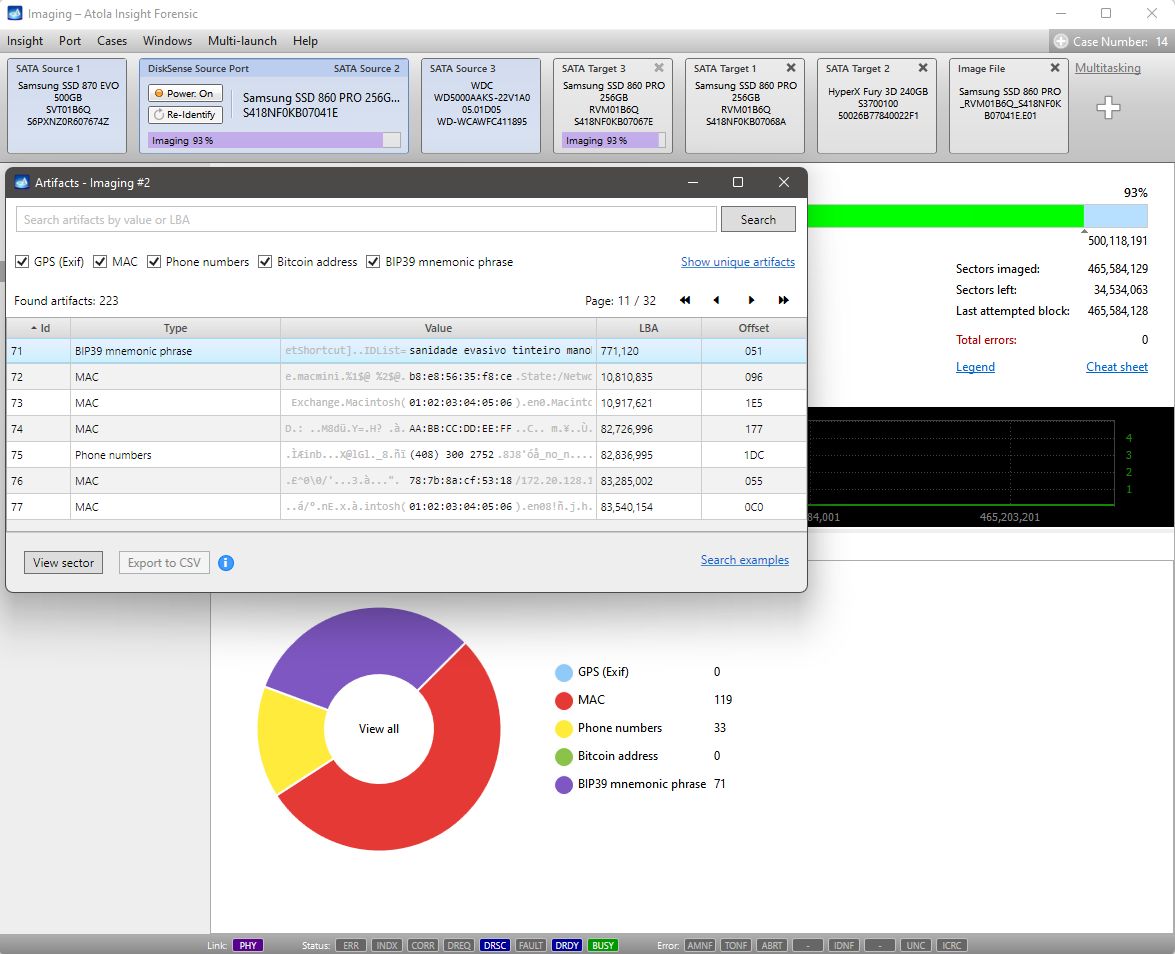
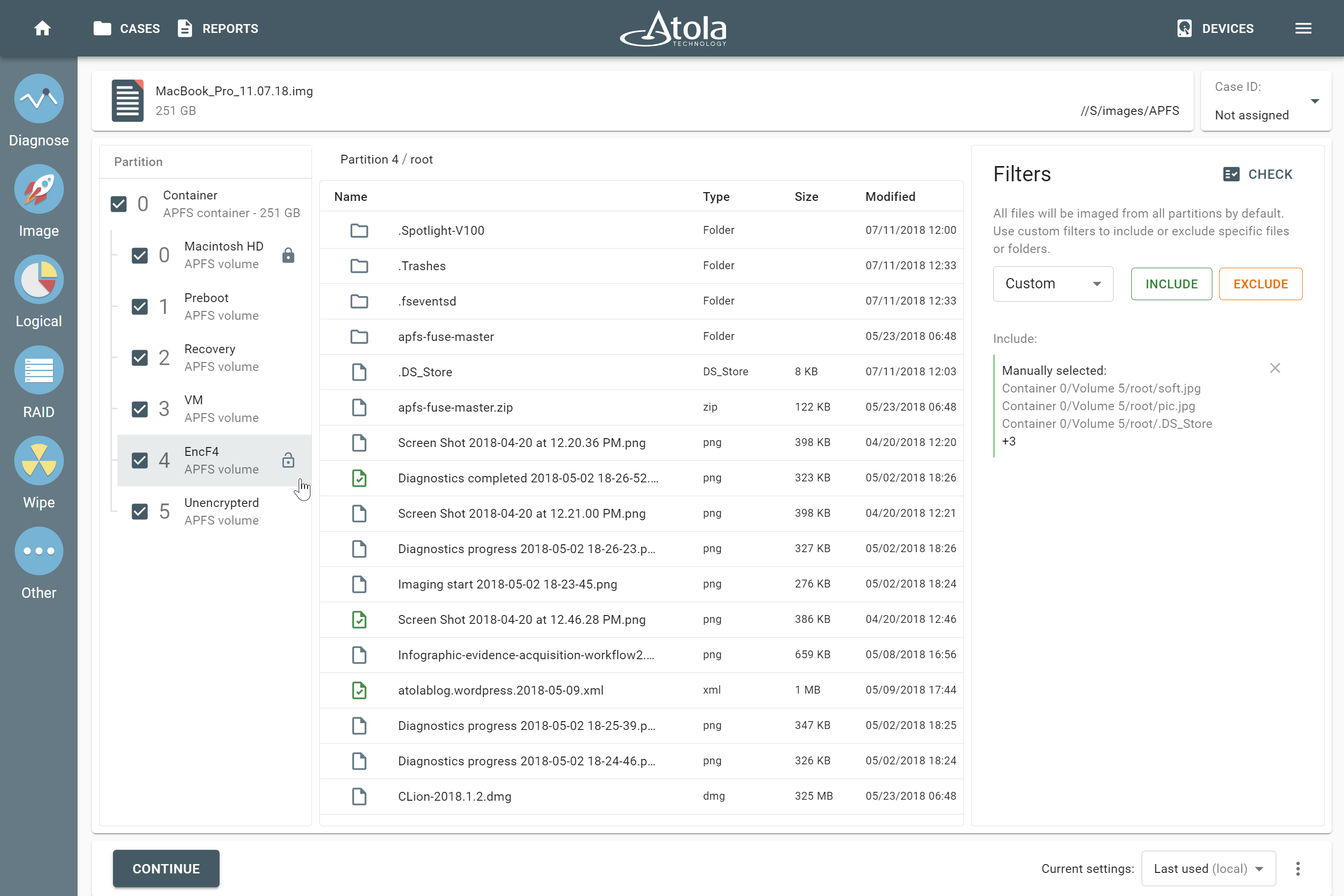
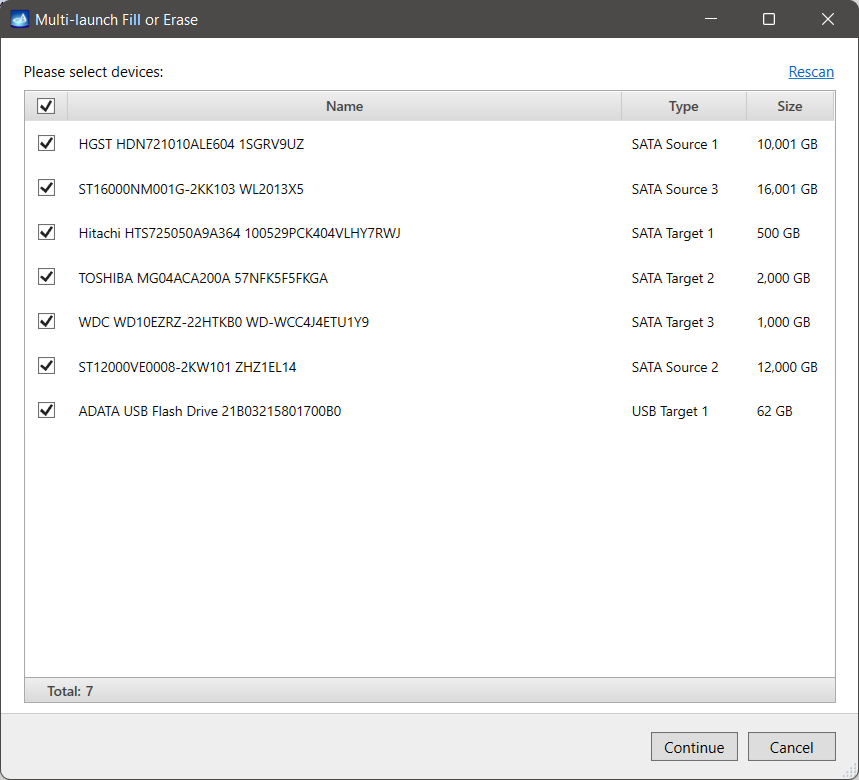
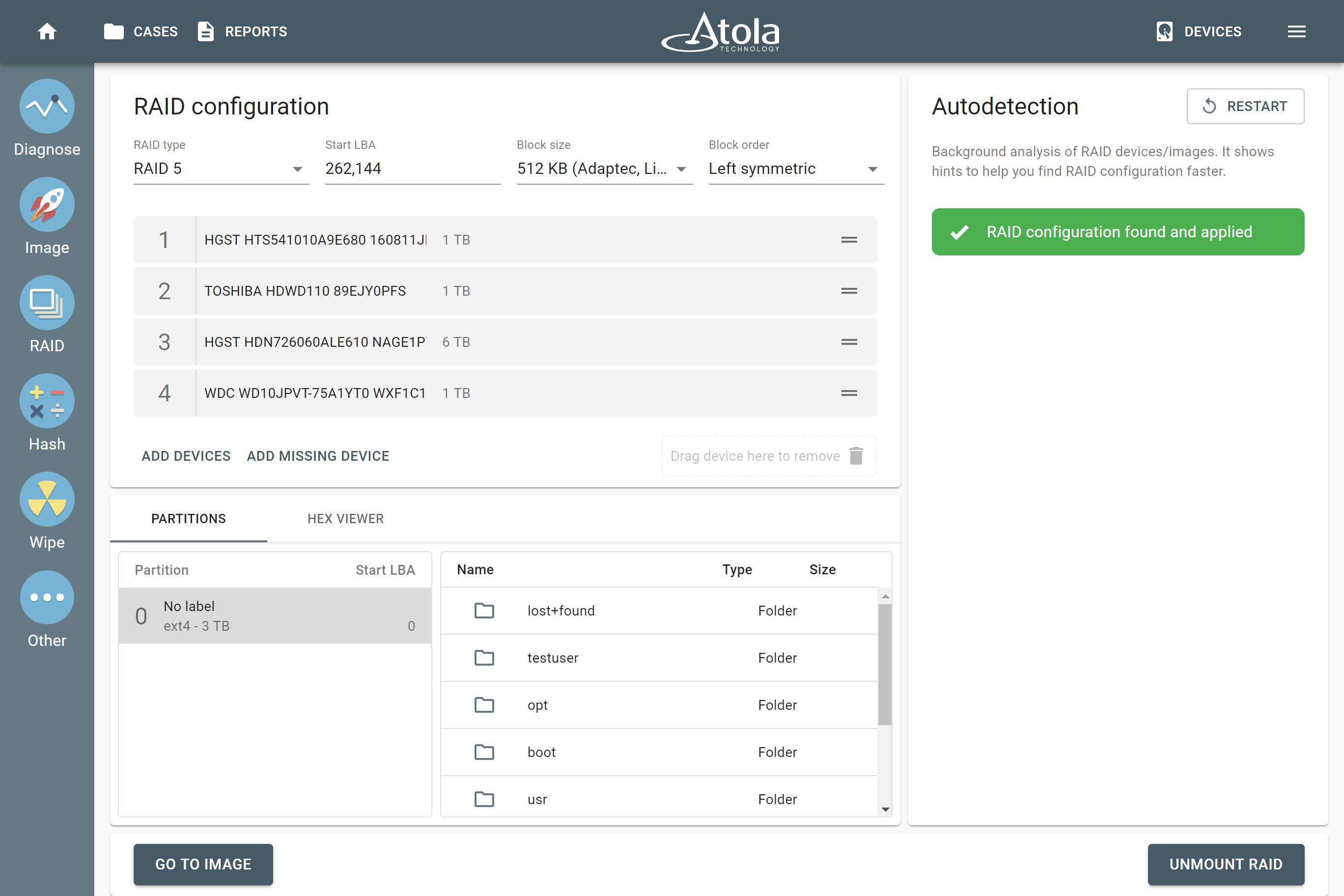
We’re going live with a new update for Atola Insight Forensic. Version 5.3 is packed with new features, has received a decent performance boost, and broadened its multitasking capabilities. Here’s our top picks: Cryptocurrency artifacts search: BIP39 mnemonic phrase, Bitcoin and Ethereum wallet addresses. New wiping methods for NVMe drives: Format NVM and Sanitize. Multi-launch of Automatic checkup, Artifact finder, Locate sectors, and Calculate hash. Let us show you the new opportunities they bring and how these new features can simplify your work! Search cryptocurrency artifacts on the fly Insight Forensic is much more than simple imaging software. It supports copying of damaged drives and manages 3 parallel imaging sessions Read more…