How often are you faced with a case with multiple individual devices with different interfaces (HDDs, SSDs, NVMe, USB, etc.) or a whole RAID array? If all you have on your hands is one imager with no parallel imaging capacity, it can result in a prohibitive processing timeline. To help you tackle such cases, we equipped TaskForce with huge performance capacity, backed by server-class hardware: TaskForce handles 12+ parallel imaging sessions on its 18 ports. In this blog, we show how the range of sources and targets you can use for imaging.
Atola TaskForce’s configurability: the range of source and targets
The product has been designed with the configurability, flexibility, and scalability in mind. It all makes TaskForce highly productive for various types of image acquisition:
- drive-to-drive
- drive-to-network
- file-to-drive
- RAID reassembly and image acquisition
- imaging to a file on a target drive
- imaging to a file on an encrypted target drive
Use as many of TaskForce’s 18 ports as you want to boost evidence acquisition: 6 SATA, 6 SATA/SAS, 4 USB, IDE, and Extension port (for Thunderbolt/Firewire, M.2 SSD including NVMe, Apple PCIe SSD devices).
All ports are switchable between Source and Target modes. Therefore, it allows you to configure the system to fit your needs at the moment. The Source mode is hardware write-protected.

Now let’s delve a little bit into each of the image acquisition options you have.
Drive-to-drive imaging
All you need for your drive-to-drive imaging session is the evidence drive and a target drive, connected to ports in the appropriate modes. Atola TaskForce allows imaging to up to 5 targets at a time at the top native speeds of good drives and supporting data recovery from damaged ones.
Drive-to-drive imaging is the fastest option of all. Certainly, it is particularly fast when imaging from one SSD to another.
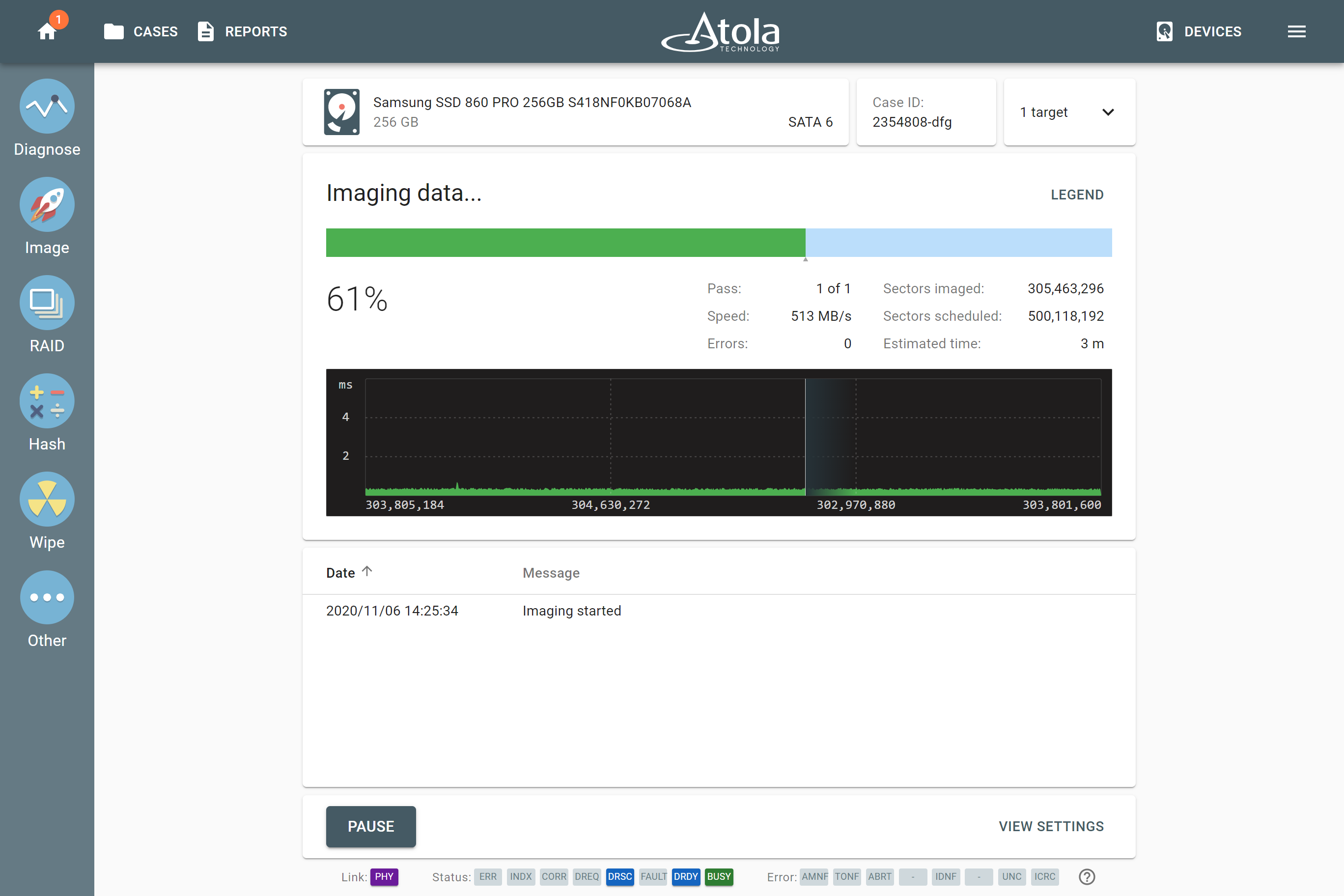
Pro Tip: TaskForce can run 6 parallel SSD-to-SSD sessions with hash being calculated with no penalty on the top native speeds of the drives.
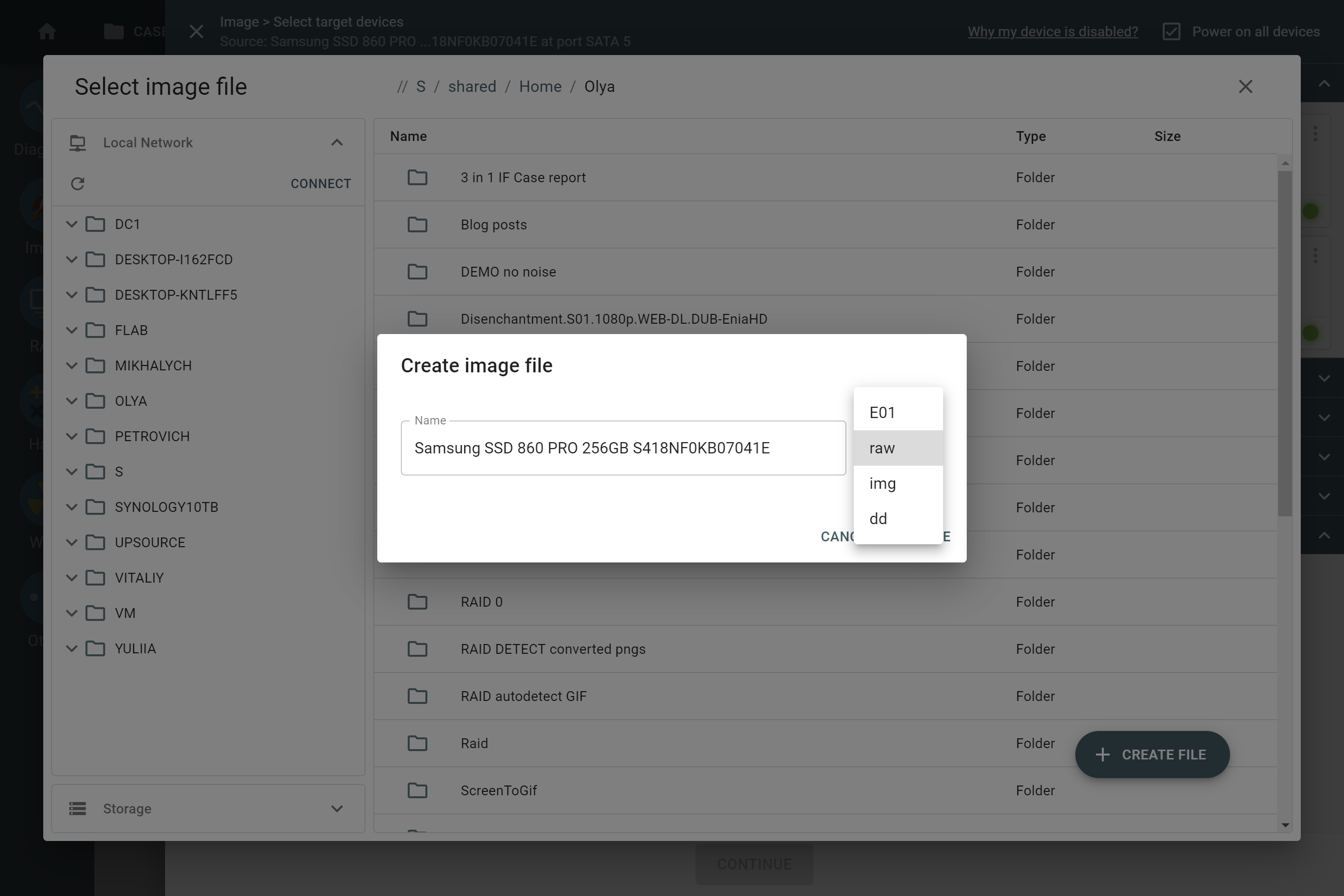
Drive-to-file imaging
When you want to create a file image, you have two main options:
- Image to a network server
- Image to a target drive
Types of supported file images:
- RAW
- E01
- AFF4 (expected to be released in the next firmware update)
Imaging to a file on a network server
With TaskForce, there are two 10Gbit Ethernet ports at your disposal. So, we highly recommend using 10Gbit network when imaging to a network server.
Bear in mind that imaging performance depends on multiple external factors like network speed, current network workload, write speed of server’s drives. Therefore, each of these factors can become a bottleneck that prolongs the imaging.
Pro Tips:
1. Make sure the server’s file system supports sparse files. Sparse files save space and time via optimized saving of sector ranges containing binary zeroes.
2. Imaging to an E01 compressed file can save you lots of time if the evidence drive contains unencrypted partitions. TaskForce has a powerful server-grade Xeon CPU, which easily handles compression of E01 chunks on-the-fly.
3. Imaging to a RAW target file is the best option when you face a severely damaged drive. The imaging engine will take advantage of the multi-pass system and its smart settings.
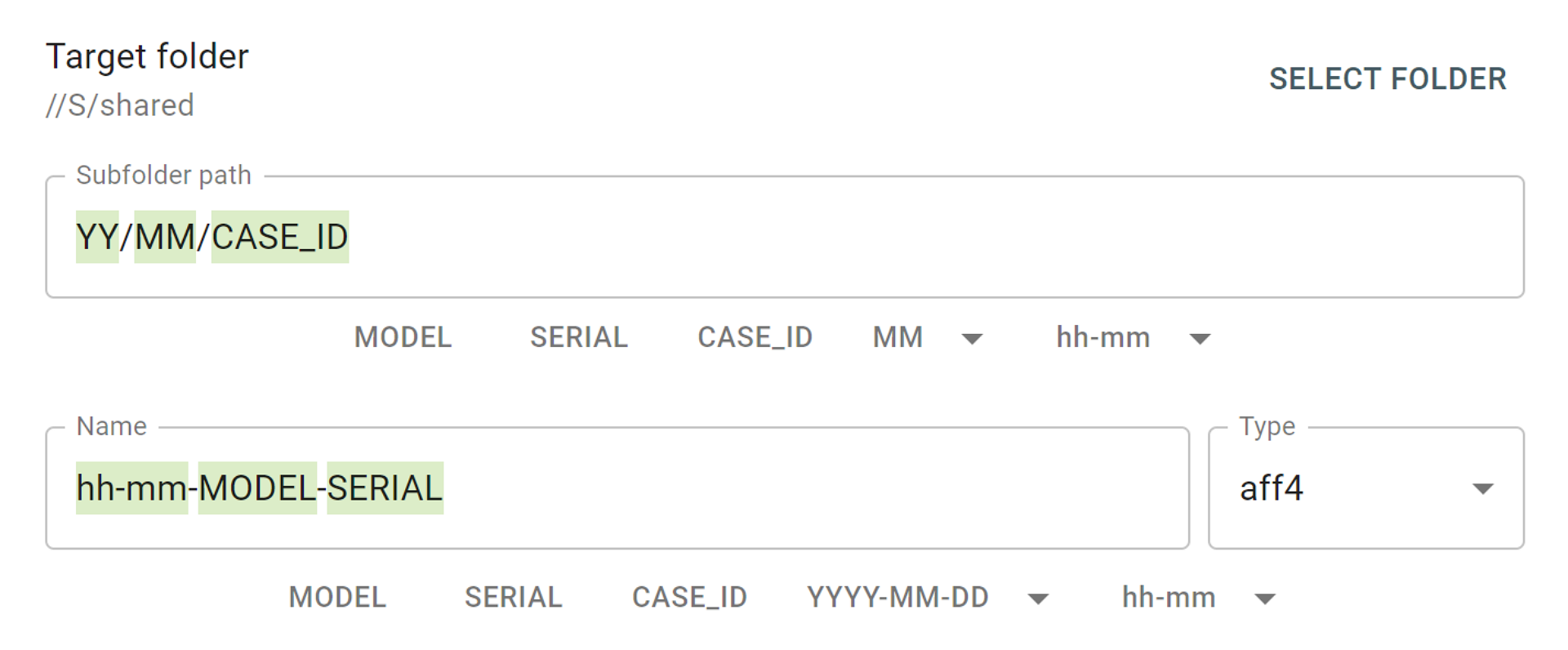
Imaging to a file on target drive
To be able to image to a file on target drive, one must configure the target to Storage mode. While reconfiguring the drive, TaskForce formats it to exFAT with 32 MB cluster size for optimized imaging speed. Once in Storage mode, the target drive serves as a destination for multiple images.
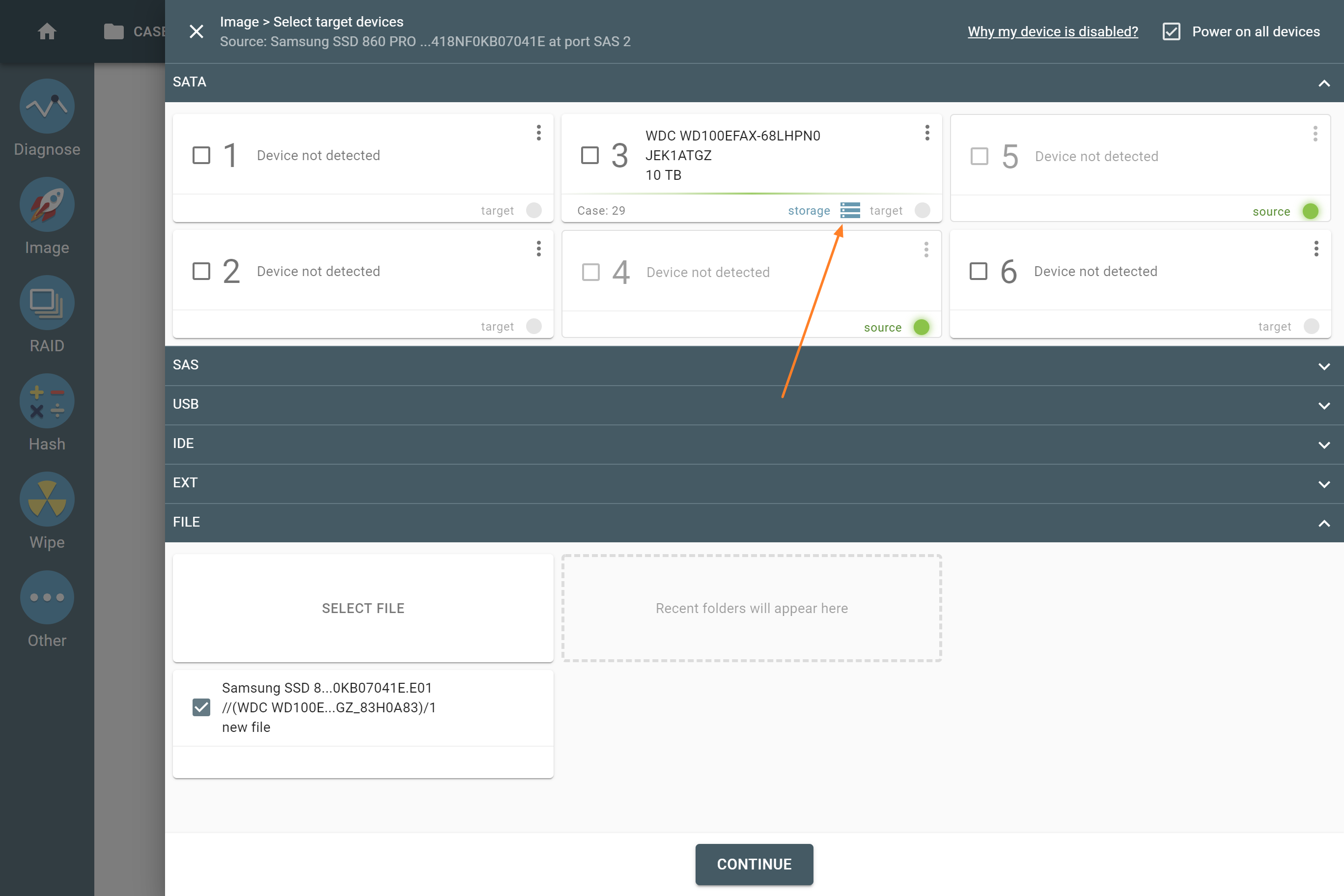
With Atola TaskForce 2020.1 and subsequent firmware versions, it is possible to image into files on an encrypted target drive. If you opt for it, the system creates an encrypted exFAT partition using VeraCrypt with a 256-bit AES algorithm on the target drive, which you lock with a password.
With encryption, your images are stored securely for storage transportation.
File-to-drive imaging
When you select an image file as an imaging source and a drive as the target, it creates an identical copy of the original evidence drive in a forensically sound way.
The feature works equally well with all supported image file types: E01, RAW, AFF4 (support of AFF4 is coming in the next firmware update).
Meanwhile, your source file can be located anywhere:
- network shared folder
- NAS
- encrypted or unencrypted target drive (Storage)
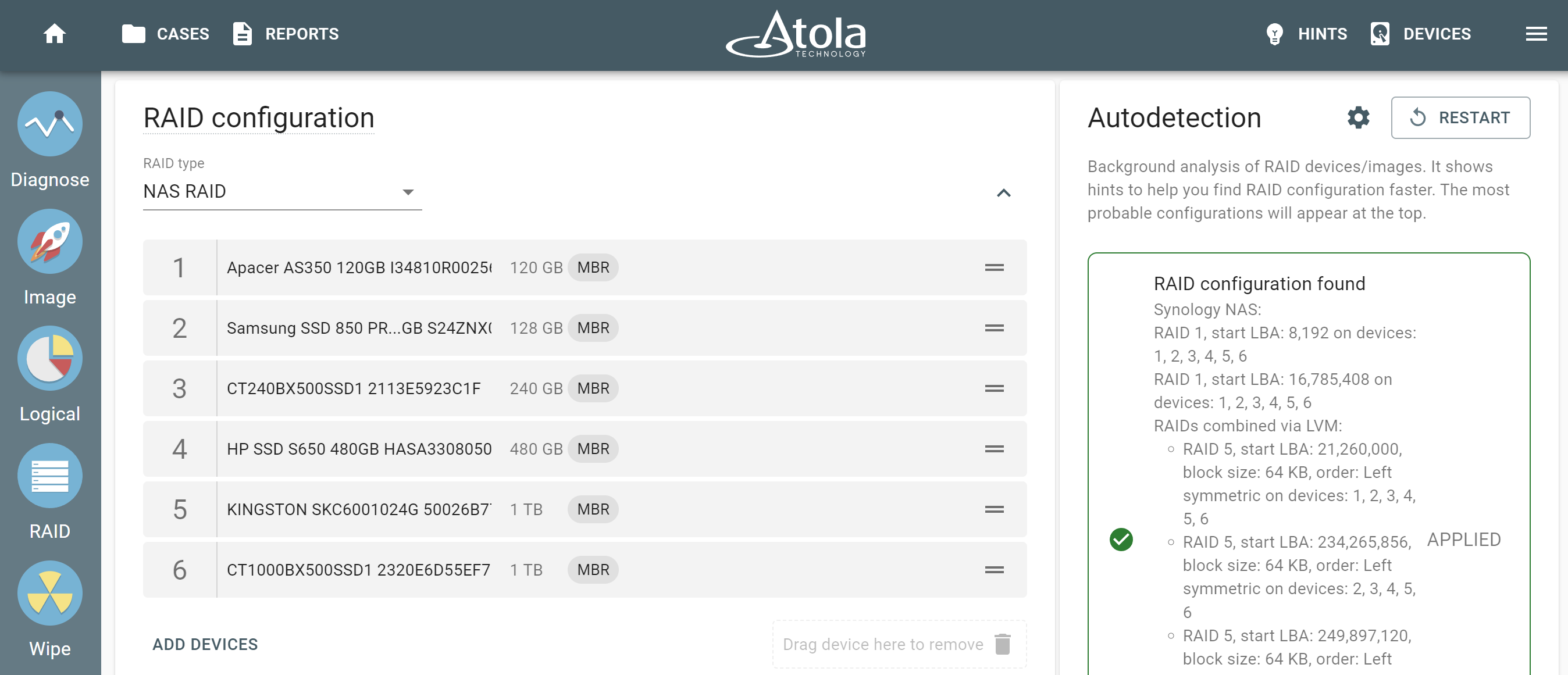
RAID image acquisition
RAID Virtual Device is a special type of imaging source you can assemble with the help of TaskForce.
2020.7 firmware equipped TaskForce with the new capability to assemble drives and/or forensic image files back into RAID arrays, automatically detect their configuration and create a forensically sound image of the volumes or the array in its entirety.
Whenever you are trying to assemble and image a source RAID 5 array, which has one drive missing or heavily damaged, Atola TaskForce uses RAID 5 redundancy to create a complete image of the RAID.
Pro Tip:
Imaging RAID 5 or RAID 1 consisting of drives with bad sectors is possible thanks to these RAIDs’ inherent parity. When a bad block is encountered on one of the RAID’s devices, reading of corresponding blocks other RAID devices or corresponding parity blocks is performed to complete the missing data.
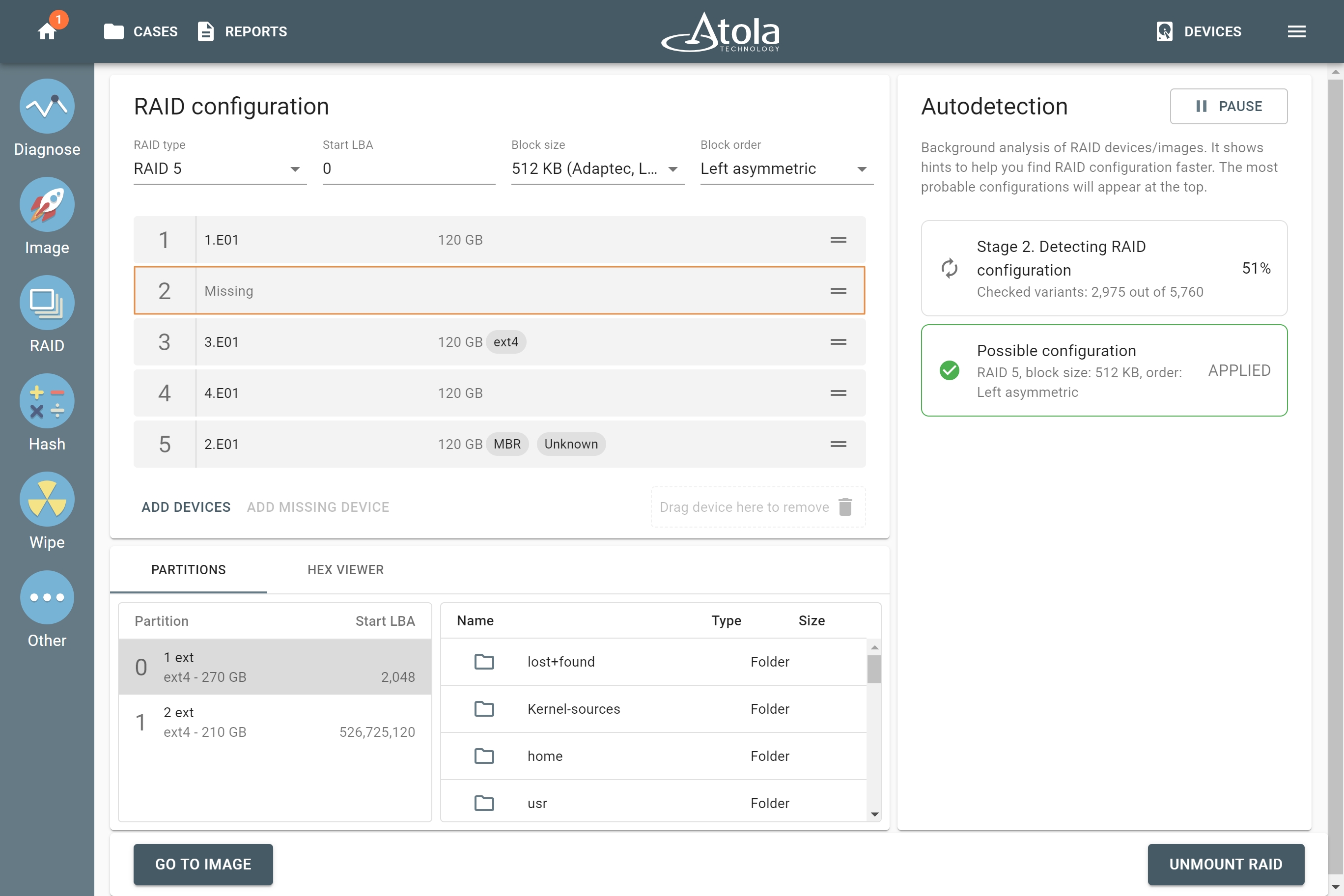
Atola TaskForce is so handy that you can also image the selected partitions of a RAID array. As a result, you obtain an image of the evidence faster.
Summary
The whole range of sources and targets to be imaged in TaskForce and its parallel capabilities are impressive. In other words, do not hesitate to start 12 or more imaging sessions with any types of selected sources and targets!
Our engineers keep developing new features to help forensic examiners handle the most challenging acquisition jobs. Certainly, we strive to create solutions that save time and energy for our customers that they can focus on other stages of an investigation.
In addition, the key vectors of TaskForce development are:
- optimization of running parallel imaging sessions
- enhancing RAID image acquisition
- adding support of new file system types and encrypted partitions
- enhancing support of damaged drives
- supporting new forensic image file containers (AFF4)
- RAID imaging made easy with TaskForce - May 3, 2022
- Image. Anything. Fast.What makes TaskForce the ultimate forensic imager - February 9, 2022
- RAID configuration detection in Atola TaskForce - April 7, 2021